Advancements and Challenges in Network Security Certification
Explore the latest advancements and key challenges in network security certification, shaping the future of cybersecurity.

Network security is now the top organizational priority in the digital age due to the increase in cyber threats. It is now vital for startups and large organizations alike to protect sensitive data from unwanted attacks. As a result, there has been a significant increase in the demand for certified network security professionals as businesses look for specialists who can successfully repel cyberattacks and deploy strong security measures.
Network security certification programs have become vital pathways for professionals aiming to prove their competence and improve their skills in the face of this increased demand. However, as technology advances quickly and attack vectors become more complex, professionals find it difficult to stay up to date on the latest developments and choose the most appropriate certification paths to satisfy industry standards.
The Challenges Faced in Network Security Certification
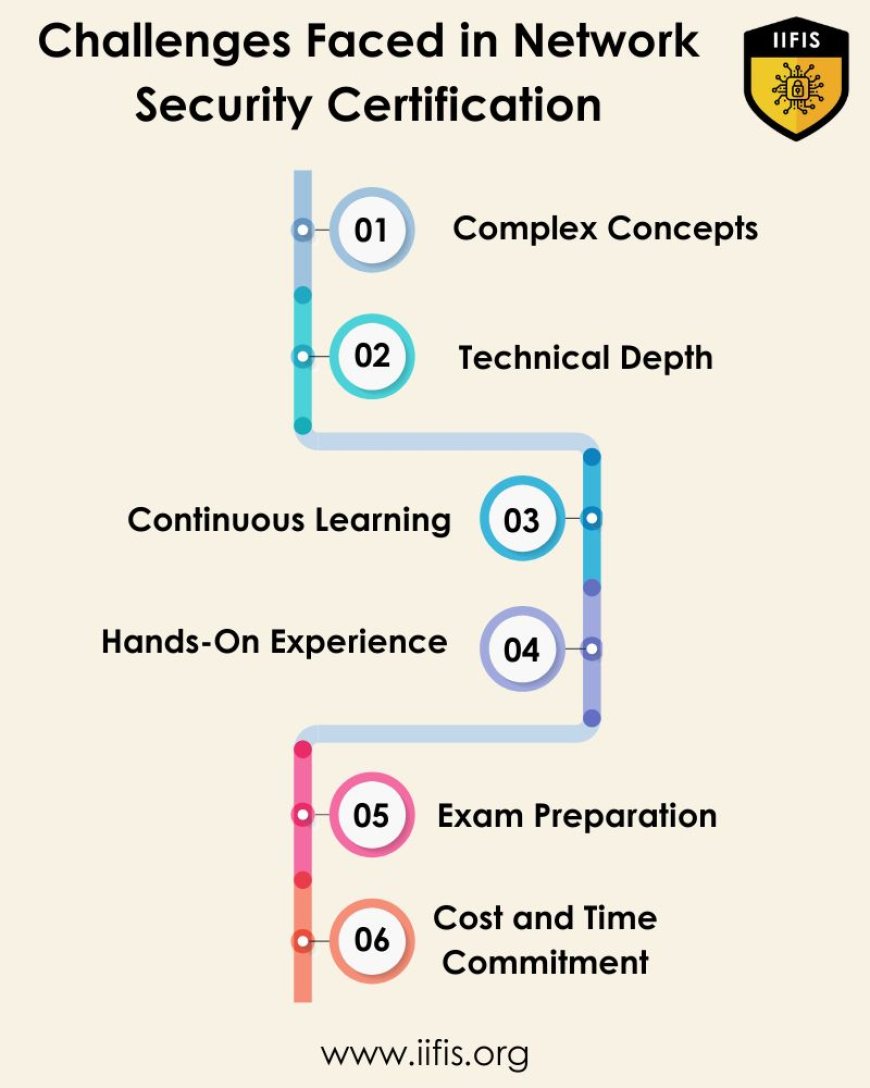
The path to network security certification is filled with difficulties that must be carefully considered and overcome with persistence to be completed. Here is a thorough examination of the challenges that people could experience:
-
Complex Concepts:
Network security includes a wide range of complex ideas and technology, such as intrusion detection systems and encryption techniques. Many find that to completely understand these ideas' intricacies and implications in practical situations, they must be understood with time and thorough study.
-
Technical Depth:
Gaining network security certification demands an in-depth understanding of technological protocols and methods. People need to become acquainted with protocols such as TCP/IP, DNS, and VPNs, in addition to the internal operations of routers, firewalls, and other network devices. Because of this technical depth, analyzing and implementing security protocols efficiently requires both academic understanding and practical experience.
-
Continuous Learning:
Network security is a dynamic field where new dangers and flaws appear at a startling rate. Keeping up with the most recent security trends, technology, and best practices is crucial. This requires a lifelong learning commitment, whether through independent research, professional development programs, or industry certifications.
-
Hands-On Experience:
In the field of network security, practical experience is invaluable, even while theoretical knowledge serves as a basis. Crucial to developing one's abilities are doing security assessments, getting practical experience with security tools, and modeling cyberattacks. However, it can be difficult to get access to the tools and chances needed for real-world applications, particularly for people who are knowledgeable in the area.
-
Exam Preparation:
Getting certified in network security frequently requires passing difficult and extensive exams. These tests, which necessitate much preparation and practice, evaluate candidates' understanding of a broad range of topics. Success requires the development of efficient study techniques, the availability of reliable study resources, and the allocation of sufficient time for review.
-
Cost and Time Commitment:
Earning a network security certification is an important time and financial commitment. Exam fees, study guides, instruction, and hands-on testing facilities are just a few of the expenses that may mount up rapidly. In addition, studying for certification tests requires a significant time investment, particularly for people who manage work and personal commitments.
What are the recent advancements in network security certification programs?
-
Integration of Cloud Security: Many certification programs now incorporate modules or specialties in cloud security due to the growing popularity of cloud computing. The increasing significance of protecting cloud-based data, apps, and systems from cyberattacks appears in this integration.
-
Focus on Zero Trust Architecture: Zero Trust Architecture (ZTA) principles are becoming increasingly important in network security certification processes. ZTA takes a rigorous "never trust, always verify" stance when it comes to network security, demanding constant verification and authorization from all users and devices that access resources, no matter where they are in the world.
-
Emphasis on DevSecOps: Certification programs include DevSecOps ideas as more firms adopt DevOps approaches for software development and deployment. To make sure that applications are secure by design means integrating safety protocols across the whole software development lifecycle, from design and coding to testing and deployment.
-
Inclusion of Threat Intelligence and Analytics: To assist professionals in understanding and mitigating cybersecurity threats, threat intelligence, and analytics modules are being integrated into certification programs. This involves employing predictive analytics and data-driven insights to proactively detect and address possible security-related problems.
-
Expansion into IoT Security: IoT security is becoming a more important topic in certification processes as a result of the growth of Internet of Things (IoT) devices. This means being aware of the particular security risks that Internet of Things devices provide, such as software flaws, shoddy identification systems, and the absence of encryption standards.
-
Focus on Compliance and Regulatory Standards: More focus is being placed on compliance and regulatory requirements like GDPR, HIPAA, and PCI DSS in network security certification programs. Professionals must comprehend the legal and regulatory frameworks on data protection and privacy. They also have to implement appropriate security protocols to ensure compliance.
Improving Network Security Certification Programs
Real-World Application:
-
Improve the number of practical, hands-on activities and case studies in certification programs. This helps students to better prepare for cybersecurity difficulties they might face in their jobs by allowing them to apply theoretical knowledge to practical situations.
Specialized Tracks:
-
Provide network security certifications or specialty programs with a special focus on cloud, IoT, or incident response security. As a result, experts may broaden their knowledge in particular fields and maintain their relevance in the quickly changing cybersecurity world.
Continuous Updates:
-
Update course materials frequently to take into account new developments in cybersecurity threats, trends, and technology. By doing this, certification programs are kept up-to-date and in line with industry standards.
Industry Partnerships:
-
Work together to create certification programs that satisfy industry standards and requirements with cybersecurity companies, professional associations, and industry partners. These collaborations can offer valuable information and useful tools to improve the caliber and applicability of programs.
Soft Skills Training:
-
Provide instruction in soft skills including teamwork, communication, and problem-solving in certification programs. Strong interpersonal skills are just as important for effective cybersecurity workers as technical expertise when it comes to working with colleagues and communicating security dangers.
Network security certification programs are crucial to coping with the growing danger of cyberattacks. Recent developments, including integrating cloud security and promoting Zero Trust Architecture, demonstrate industry commitment to staying ahead of changing dangers despite obstacles like technological complexity and the need for constant learning. Program efficacy can be further increased with additions like specialty tracks, real-world applications, and soft skills training. These programs are crucial for strengthening cybersecurity resilience and protecting businesses from contemporary online dangers because they provide professionals with current knowledge and practical skills. Network security certification programs can fulfill the increasing need for qualified experts in a dynamic digital environment with continued improvements.
























