How Web Application Firewall Detects and Prevents Attacks
Learn how a Web Application Firewall (WAF) detects and blocks attacks by analyzing traffic, filtering threats, and protecting web applications effectively.

As a web application expert, I know how vital security is for protecting digital assets. A Web Application Firewall (WAF) is a key defense mechanism that safeguards web apps from threats like SQL injections, XSS, and DDoS attacks. By monitoring and filtering malicious traffic, WAFs provide real-time protection, ensuring the integrity, availability, and security of your applications against evolving cyber threats.
What Is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security system designed to monitor, filter, and block malicious HTTP/HTTPS traffic to and from a web application. Unlike traditional firewalls that protect networks, WAFs specifically focus on the application layer, where many cyber threats originate.
WAFs are crucial for defending against common web attacks such as SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks. By analyzing incoming traffic, WAFs can identify suspicious patterns and take proactive measures to prevent breaches, enhancing overall web application security.
The Core Functionality of a Web Application Firewall
A Web Application Firewall operates through a combination of rule sets, traffic monitoring, and threat intelligence. Here’s how it works:
-
Traffic Inspection: WAFs inspect incoming and outgoing web traffic in real-time.
-
Rule-Based Filtering: They apply predefined security rules to detect known attack signatures.
-
Behavioral Analysis: Advanced WAFs use machine learning to identify unusual behavior that may indicate a potential threat.
-
Response Mechanisms: Once a threat is detected, the WAF can block the malicious request, log the incident, or alert security teams for further investigation.
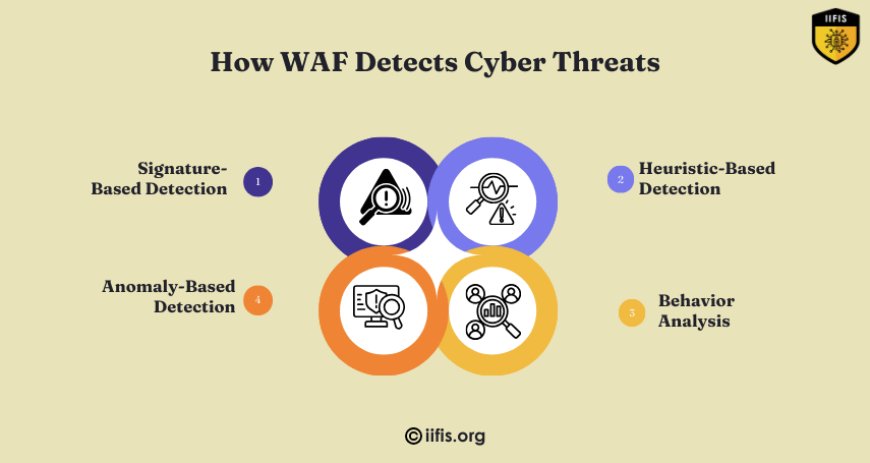
How WAF Detects Cyber Threats
Detection is the first step in preventing cyberattacks. A Web Application Firewall employs several techniques to identify threats effectively:
Signature-Based Detection
WAFs compare incoming traffic against known attack signatures stored in their databases. This method is highly effective for identifying common threats like SQL injections and XSS attacks.
Anomaly-Based Detection
Anomaly detection involves setting a baseline of normal traffic behavior. Any deviation from this baseline, such as unusual spikes in requests, triggers an alert. This method helps detect zero-day attacks and sophisticated threats.
Heuristic-Based Detection
Heuristics analyze the structure and behavior of requests to identify potentially malicious activity, even if it doesn’t match known attack signatures. This approach is useful for catching new or evolving threats.
Behavior Analysis
Advanced WAFs use machine learning algorithms to analyze traffic patterns over time. This helps identify complex attack strategies that might not trigger traditional detection methods.
Preventing Attacks with a Web Application Firewall
Once a potential threat is detected, the Web Application Firewall takes immediate action to prevent the attack from reaching the application. Here’s how it handles different types of threats:
Blocking Malicious Requests
The WAF can automatically block IP addresses or specific requests that match known attack patterns, preventing them from accessing the application.
Rate Limiting
In the case of DDoS attacks, WAFs can limit the number of requests from a single source, reducing the impact of the attack.
Virtual Patching
WAFs can apply virtual patches to vulnerable applications, providing protection even if the underlying software hasn’t been updated. This is especially useful for addressing known vulnerabilities in real-time.
Redirecting Suspicious Traffic
Some WAFs redirect suspicious traffic to honeypots or sandbox environments for further analysis, preventing potential threats from affecting live applications.
Measures to Strengthen Firewall Security
To maximize the effectiveness of a Web Application Firewall, it’s essential to implement additional security measures:
-
Regular Updates: Keep WAF software updated with the latest threat intelligence and security patches.
-
Strong Authentication: Use multi-factor authentication (MFA) for access control to prevent unauthorized configuration changes.
-
Network Segmentation: Limit WAF exposure by segmenting networks, reducing the risk of lateral movement in case of breaches.
-
Traffic Encryption: Ensure all traffic between the WAF and web applications is encrypted using protocols like TLS/SSL.
-
Custom Rules and Policies: Tailor security rules to specific application needs, enhancing protection against unique threats.
Best Practices for Optimizing Web Application Firewall Performance
While WAFs are powerful security tools, optimizing their performance ensures they work efficiently without affecting application speed:
-
Fine-Tune Security Rules: Regularly review and adjust rules to reduce false positives and improve accuracy.
-
Load Balancing: Distribute traffic across multiple WAF instances to prevent performance bottlenecks.
-
Monitoring and Logging: Continuously monitor traffic logs for anomalies and performance issues.
-
Automated Threat Response: Enable automated responses for known threats to reduce manual intervention.
-
Regular Security Audits: Conduct periodic audits to evaluate WAF effectiveness and identify areas for improvement.
Benefits of Using a Web Application Firewall
Implementing a Web Application Firewall offers numerous benefits for organizations, including:
-
Enhanced Security: Provides robust protection against a wide range of web-based attacks.
-
Data Privacy: Safeguards sensitive data from breaches and leaks.
-
Compliance: Helps meet regulatory requirements for data protection (e.g., GDPR, PCI-DSS).
-
Reduced Downtime: Mitigates the risk of downtime caused by cyber attacks, ensuring business continuity.
-
Real-Time Monitoring: Offers continuous monitoring and immediate threat response.
Choosing the Right Web Application Firewall
When selecting a Web Application Firewall, consider the following factors:
-
Deployment Options: Decide between cloud-based, on-premises, or hybrid solutions based on your organization’s needs.
-
Scalability: Ensure the WAF can handle increasing traffic volumes without performance issues.
-
Customizability: Look for flexible rule sets that can be tailored to specific security requirements.
-
Integration Capabilities: The WAF should integrate seamlessly with existing security tools and infrastructure.
-
Support and Updates: Choose a provider that offers regular updates and robust customer support.
A Web Application Firewall is essential for keeping web applications safe. Getting an Application Security Certification helps you build the skills needed to protect apps from new and growing threats, making you more effective in cybersecurity. It gives you the knowledge to apply strong security measures with confidence.
























