Why Web Application Security is Crucial for You
Web application security is essential to protect user data, prevent cyberattacks, and ensure a safe online experience, safeguarding both businesses and users.

As an expert in the field of cybersecurity, I can tell you that the security of your web applications is more critical now than ever before. With an increasing number of cyberattacks targeting businesses of all sizes, ensuring the security of your web applications should be a top priority. Whether you’re running an e-commerce site, managing sensitive customer data, or simply offering online services, the consequences of neglecting web application security can be severe
Understanding the Importance of Web Application Security
Web application security refers to the measures taken to safeguard web applications from malicious attacks and unauthorized access. With web applications becoming an essential part of everyday life, they are prime targets for cybercriminals. Hackers exploit vulnerabilities in applications to gain access to sensitive data, disrupt services, or even hijack systems for malicious purposes.
The importance of web application security is multi-fold:
-
Protecting Sensitive Data: Web applications often store valuable personal information such as usernames, passwords, credit card numbers, and health data. A breach of this information could lead to identity theft, fraud, or worse.
-
Maintaining business continuity: Many businesses rely on web applications for customer interactions, transactions, and internal operations. A security breach could result in system downtime, loss of revenue, and damage to the company’s reputation.
-
Compliance with Regulations: Data protection laws such as GDPR, HIPAA, and PCI-DSS require businesses to secure personal and financial information. Non-compliance can lead to hefty fines and legal issues.
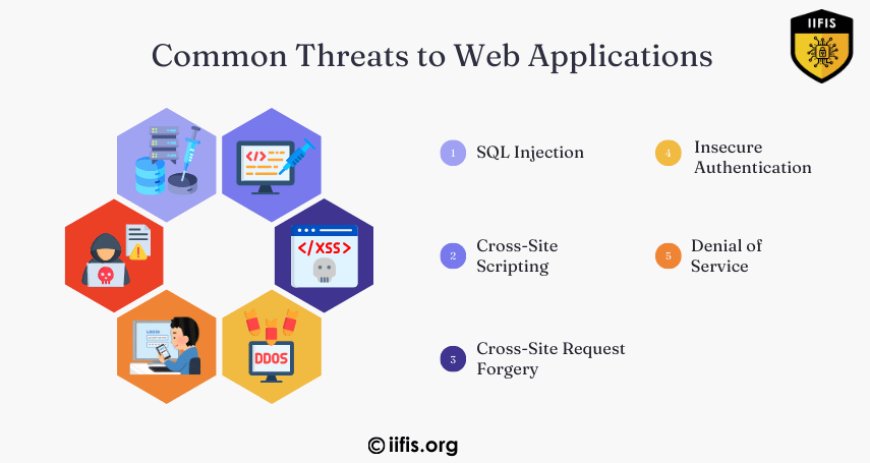
Common Threats to Web Applications
Web applications face a wide array of threats, some of which are well-known, while others are more subtle. Understanding these threats is crucial for building a secure application. Here are some of the most common web application vulnerabilities:
-
SQL Injection: This attack occurs when malicious SQL queries are inserted into an input field to manipulate or access data in a web application's database. A successful SQL injection can expose sensitive data, such as passwords and payment information.
-
Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into a webpage that gets executed by unsuspecting users. This can lead to the theft of user credentials or data.
-
Cross-Site Request Forgery (CSRF): CSRF exploits a trusted user's session to perform unwanted actions, such as transferring funds or changing passwords without their knowledge.
-
Insecure authentication: weak authentication mechanisms are common targets for attackers. They exploit poor password management or faulty session handling to gain unauthorized access.
-
Denial of Service (DoS): DoS attacks aim to overwhelm a web application with traffic, making it unavailable to legitimate users.
Best Practices for Web Application Security
Implementing robust web application security involves a combination of proactive strategies and ongoing vigilance. Here are some key best practices to protect your web applications:
-
Input Validation and Sanitization: Always validate and sanitize user input to ensure that only safe and expected data is processed. This prevents malicious code from being executed and reduces the risk of SQL injection and XSS attacks.
-
Use HTTPS for encryption: HTTPS encrypts the data exchanged between the client and the server, ensuring that sensitive information, like login credentials and credit card details, is protected from being intercepted by attackers.
-
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring users to provide additional verification beyond just a password. This makes it harder for attackers to gain unauthorized access.
-
Keep Software and Dependencies Up to Date: Regularly updating web applications and their underlying software components helps patch known vulnerabilities and protect against new exploits.
-
Web Application Firewalls (WAF): WAFs monitor and filter HTTP requests to block malicious traffic before it reaches the application. They can help prevent common attacks such as SQL injection and XSS.
-
Regular security audits and penetration testing: Regularly testing your web application for security flaws is essential. Penetration testing simulates real-world attacks, helping identify and fix vulnerabilities before they are exploited.
The Consequences of Poor Web Application Security
Failing to secure your web applications can lead to disastrous consequences, both for businesses and individual users.
-
Data Breaches: Sensitive personal and financial data can be exposed, resulting in identity theft and financial loss. For businesses, this can mean the loss of customer trust and costly legal repercussions.
-
Reputation Damage: A security breach can significantly harm a company’s reputation. Customers may abandon a brand if they feel their data is not being protected adequately, and bad press can be hard to overcome.
-
Financial Loss: Beyond the direct costs of dealing with a breach, businesses could face fines from regulatory bodies if they fail to comply with data protection laws. Furthermore, system downtime from attacks can lead to revenue loss.
-
Intellectual Property Theft: Web applications often store proprietary information, trade secrets, and other intellectual property. A breach could result in valuable business assets being stolen or compromised.
How to Build a Secure Web Application
Building a secure web application involves integrating security measures at every stage of development. Here’s how to ensure your application is secure from start to finish:
-
Security by Design: From the initial design phase, ensure that security considerations are integrated into every aspect of the application. Use secure coding practices and focus on identifying potential risks early on.
-
Layered Defense: Employs multiple layers of security, such as encryption, firewalls, and access controls. A layered approach ensures that even if one defense mechanism fails, others will still protect the application.
-
Security Testing: Incorporate security testing into your development process. Regularly test for vulnerabilities using automated tools and manual code reviews. Penetration testing should also be part of your ongoing security strategy.
-
Continuous Monitoring: Once the application is live, continue to monitor it for unusual activity and potential vulnerabilities. Implement intrusion detection systems (IDS) and regularly update your security protocols.
Web application security is critical for protecting sensitive data, ensuring business continuity, and complying with regulations. Neglecting security can lead to data breaches, financial loss, and reputational damage. By understanding the risks and implementing best practices like secure coding, regular testing, and continuous monitoring, you can safeguard your applications from evolving threats. Prioritizing web application security is essential to maintaining trust and protecting your business























