The Role of Encryption in Mobile Application Security
Learn how encryption boosts Mobile Application Security by safeguarding data in transit and at rest, protecting sensitive information from cyber threats and unauthorized access.
As someone deeply involved in application security, I’ve seen how mobile technology's rapid growth brings new security challenges. One major concern is Mobile Application Security, especially with apps managing so much sensitive data. In my experience, encryption isn’t just a technical detail; it’s a fundamental part of building secure, trustworthy mobile applications.
Understanding Mobile Application Security
To keep mobile apps secure, it’s important to understand what Mobile Application Security means. It’s about protecting apps from threats like malware, hacking, and data breaches. Since apps often handle personal, financial, or sensitive business data, keeping them secure is essential to avoid risks that could harm users and companies.
One of the most important ways to do this is through encryption. It helps keep data safe, whether it’s stored on a device or being sent over the internet. In a world where mobile apps are part of everyday life, understanding how encryption works is key to building secure apps.
What Is Encryption and How Does It Work?
Encryption is a method of securing data by converting it into an unreadable format using algorithms and cryptographic keys. Here’s how it works:
-
Data Transformation: Converts readable data (plaintext) into an unreadable format (ciphertext).
- Use of Algorithms: Utilizes mathematical algorithms to perform encryption.
-
Decryption: Only authorized users with the correct key can revert the data to its original form.
Encryption in Mobile Application Security:
-
Protects Sensitive Data: Safeguards login credentials, personal information, payment data, and in-app communication.
-
Minimizes Risk: Even if hackers access the device or backend, encrypted data remains unreadable.
-
Enhances Data Privacy: Ensures that user information stays secure during storage and transmission.
-
Critical for Compliance: Helps apps meet data protection regulations.
Types of Encryption in Mobile Applications
There are two primary types of encryption used in Mobile Application Security: symmetric encryption and asymmetric encryption.
-
Symmetric Encryption: In this method, both the sender and the receiver share a single key to encrypt and decrypt the data. The challenge with symmetric encryption is ensuring the secure distribution of the key.
-
Asymmetric Encryption: Also known as public-key cryptography, this method uses a pair of keys: a public key to encrypt data and a private key to decrypt it. This method enhances security by preventing the need to share a single key between parties.
Both of these encryption types play critical roles in securing mobile applications, and developers often choose the one that best fits the specific needs of the app, balancing between performance and security.
Encryption Protects Data in Transit
One of the key aspects of Mobile Application Security is protecting data while it’s being transmitted over the internet or networks. Here’s how encryption helps:
-
Secures Data Transmission: Converts data into an unreadable format during transit.
-
Prevents Interception: Even if hackers intercept the data, they can’t read it without the decryption key.
-
Common Protocols:
-
SSL (Secure Socket Layer): Encrypts data between the app and server.
-
TLS (Transport Layer Security): Provides secure communication, often used in web-based mobile apps.
-
Secure Communication Channels: Establishes a protected link between the mobile app and the server, reducing the risk of data breaches.
Encryption Protects Data at Rest
Data at rest refers to information stored on a device or server. Here’s why encryption is crucial:
-
Prevents Unauthorized Access: Ensures that stored data (like credentials and sensitive files) is not readable without the decryption key.
-
Device Security: Many modern smartphones use hardware-based encryption to automatically secure stored data.
-
App-Level Protection: Developers can integrate encryption to secure user data even if the device is lost or compromised.
-
Example: Built-in encryption features in smartphones help enhance Mobile Application Security by keeping stored data secure.
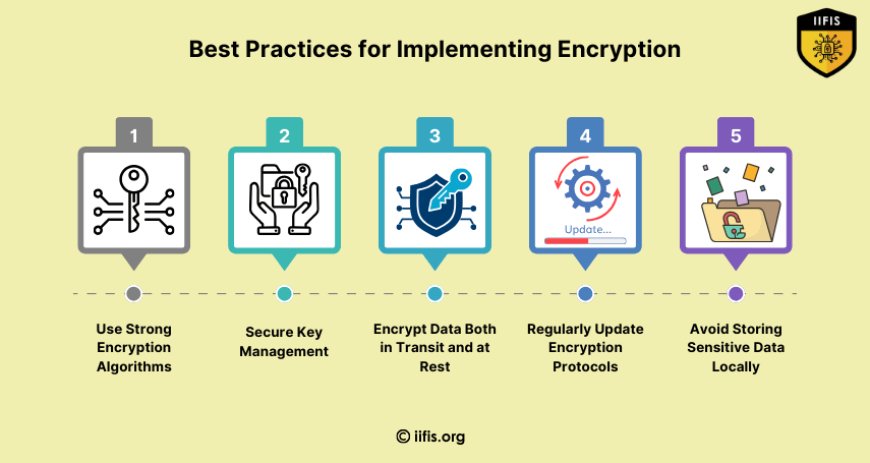
Best Practices for Implementing Encryption in Mobile Apps
To maximize the effectiveness of encryption and enhance Mobile Application Security, developers must follow best practices when implementing encryption in their mobile apps. Some key practices include:
-
Use Strong Encryption Algorithms: Always choose strong encryption algorithms like AES (Advanced Encryption Standard) with appropriate key lengths (e.g., 256 bits) to ensure the highest level of protection.
-
Secure Key Management: Key management is critical for encryption security. Never hardcode encryption keys within the app code. Instead, use secure key storage mechanisms like Android’s Keystore or iOS’s Secure Enclave to store and access keys.
-
Encrypt Data Both in Transit and at Rest: Ensure that all sensitive data is encrypted both during transmission (using SSL/TLS) and when stored on the device or server.
-
Regularly Update Encryption Protocols: As vulnerabilities in cryptographic algorithms and protocols emerge, it’s crucial to stay updated on the latest security trends and make timely updates to encryption methods.
-
Avoid Storing Sensitive Data Locally: Whenever possible, avoid storing sensitive information locally on the device. Instead, use secure servers or cloud storage that are protected by strong encryption.
By following these practices, developers can significantly improve the Mobile Application Security of their apps, making them more resilient to potential threats and attacks.
Encryption is a core component of Mobile Application Security, safeguarding data from unauthorized access and cyber threats. Whether protecting data at rest or in transit, encryption acts as a strong defense. Implementing robust encryption practices helps ensure app security and compliance.
Though encryption can pose challenges like performance impact and key management, its benefits far outweigh the drawbacks. For those looking to enhance their skills, IIFIS certifications offer practical knowledge to master encryption and stay ahead in mobile app security.























