What is penetration testing in Cybersecurity?
Learn about penetration testing in cybersecurity: a vital process that simulates cyberattacks to identify system vulnerabilities and strengthen your security defenses.

As a certified penetration tester with extensive experience, I specialize in identifying vulnerabilities within systems, networks, and applications. I will share about penetration testing, which involves simulating real-world cyberattacks to uncover weaknesses, providing businesses with actionable insights to strengthen their security defenses and safeguard critical data.
What is penetration testing in Cybersecurity?
Penetration testing is a cybersecurity key practice that involves simulating a cyberattack on a system, network, or application to identify weaknesses and vulnerabilities that could be exploited by hackers. As cyber threats continue to grow and evolve, penetration testing helps businesses strengthen their security measures and protect valuable data.
Understanding Penetration Testing
Penetration testing, also known as "ethical hacking," is a proactive security measure where cybersecurity professionals attempt to exploit weaknesses in a system or network. The goal is to identify vulnerabilities before malicious hackers can use them to gain unauthorized access. During a penetration test, the tester, or ethical hacker, simulates the tactics, techniques, and procedures that cybercriminals might use to breach a system.
Penetration testing can be performed on various systems, including networks, web applications, mobile apps, and more. It usually follows a structured approach, including planning, scanning, identifying vulnerabilities, exploitation, and reporting.
The Role of Penetration Testing in Cybersecurity
Penetration testing in Cybersecurity plays a critical role in enhancing cybersecurity for businesses. Unlike regular vulnerability scans, which only identify potential weaknesses, a certified penetration tester actively tests a system's defenses by attempting to exploit those vulnerabilities
Here are some primary roles penetration testing plays in cybersecurity:
-
Identifying vulnerabilities: Penetration testing uncovers security gaps in your network, systems, or applications that hackers could exploit.
-
Testing security measures: It helps determine whether existing security tools, such as firewalls or intrusion detection systems, can detect and prevent attacks.
-
Assessing overall security posture: By simulating real-world attacks, penetration testing provides insight into how well your security infrastructure holds up under pressure.
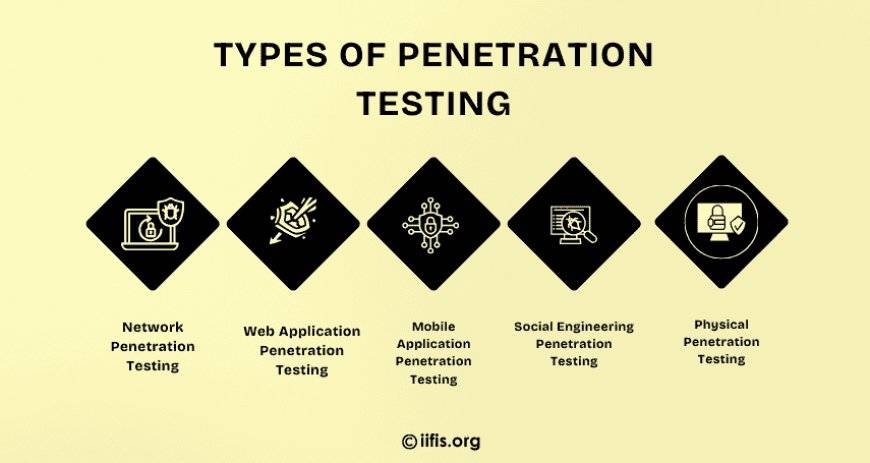
Types of Penetration Testing
Penetration testing can be classified into different types based on the scope and objectives. The most common types include:
-
Network Penetration Testing: This focuses on identifying vulnerabilities in your network infrastructure. It tests your firewall, routers, switches, and other network components to ensure they are secure against cyberattacks.
-
Web Application Penetration Testing: This type focuses on testing the security of web applications. It involves checking for vulnerabilities such as SQL injection, cross-site scripting (XSS), and other common security flaws that could be exploited by attackers.
-
Mobile Application Penetration Testing: This type assesses the security of mobile applications, identifying vulnerabilities that could lead to data breaches or unauthorized access.
-
Social Engineering Penetration Testing: This involves testing how vulnerable an organization’s employees are to phishing attacks and other social engineering tactics that trick them into revealing sensitive information.
-
Physical Penetration Testing: This tests the physical security of an organization's premises to ensure that unauthorized individuals cannot gain access to critical systems or sensitive data.
The Benefits of Penetration Testing
Penetration testing offers numerous benefits for businesses looking to protect their data and assets. Some of the key advantages include:
-
Identifying Weaknesses Early: Penetration testing helps uncover vulnerabilities before cybercriminals can exploit them. By identifying weaknesses early, organizations can patch them and reduce the risk of an attack.
-
Improving Compliance: Many industries require businesses to comply with specific security regulations (e.g., GDPR, HIPAA). Penetration testing helps ensure that your organization is compliant with these requirements and can provide documented evidence for audits.
-
Enhancing Risk Management: Penetration testing helps organizations understand the risks they face and prioritize their cybersecurity efforts based on potential impact. This enables businesses to focus on the most critical vulnerabilities first.
-
Building Trust with Clients: Conducting regular penetration testing demonstrates a commitment to security, which can enhance trust with customers and partners. It shows that you take cybersecurity seriously and are actively working to protect their data.
Penetration Testing Methodology
Penetration testing in Cybersecurity typically follows a structured methodology that involves several phases. The common stages of a penetration test include:
-
Planning and Reconnaissance: In this phase, the penetration tester gathers information about the target system, such as its network topology, operating systems, and software. This phase is crucial for identifying potential entry points and preparing for the actual testing.
-
Scanning and Enumeration: During this phase, the tester uses automated tools to scan the system for open ports, services, and other weaknesses. The goal is to identify vulnerabilities that could be exploited.
-
Exploitation: In this phase, the tester attempts to exploit the identified vulnerabilities to gain access to the system. The tester may attempt to escalate privileges, access sensitive data, or disrupt the system.
-
Post-Exploitation and Reporting: Once the tester gains access, they evaluate the extent of the damage that could be caused by the vulnerability. Finally, a detailed report is generated, outlining the vulnerabilities found, the exploitation process, and recommendations for mitigation.
How to Choose a Penetration Testing Provider
Choosing the right penetration testing provider is crucial for ensuring a successful and effective security assessment. Here are some tips for selecting the best provider for your needs:
-
Experience and Expertise: Ensure the provider has extensive experience in conducting penetration tests across different industries and technologies. Look for certified professionals, such as those with certifications like Cybersecurity certification.
-
Comprehensive Testing: Choose a provider that offers a thorough testing process, covering all aspects of your system, including network, web applications, and social engineering tactics.
-
Clear Reporting: The provider should deliver a detailed report outlining vulnerabilities, how they were exploited, and actionable recommendations for remediation.
-
Compliance Knowledge: If your business must adhere to certain regulatory standards, ensure the provider is familiar with those requirements and can help you meet them.
Best Practices After Penetration Testing
After conducting a penetration test, it's essential to act on the findings to improve your cybersecurity posture. Here are some best practices to follow after penetration testing:
-
Address Vulnerabilities: Immediately fix the vulnerabilities that were identified during the test. Patch outdated software, change weak passwords, and implement additional security controls where necessary.
-
Retest Critical Systems: After addressing vulnerabilities, consider retesting critical systems to ensure they are secure and that no new issues were introduced during the remediation process.
-
Enhance Employee Training: Penetration testing often uncovers human vulnerabilities, such as susceptibility to phishing attacks. Use the results to train employees on recognizing and avoiding social engineering tactics.
-
Continuous Monitoring: Implement continuous monitoring systems to detect any new vulnerabilities and unauthorized activities in real-time. This will help ensure ongoing protection.
penetration testing is a vital part of cybersecurity, helping businesses identify and address vulnerabilities before they can be exploited by hackers. By regularly conducting penetration tests, organizations can enhance their security, comply with regulations, and protect valuable data effectively.
























