How to Become an Application Security Expert
Learn how to become an application security expert with essential skills, certifications, and best practices to secure apps and protect sensitive data.
As an application security expert, I can tell you that becoming proficient in this field requires a combination of knowledge, practical experience, and continuous improvement. The field of application security is ever-evolving, and with the increasing number of cyberattacks, it is more important than ever to secure applications from potential threats. Here’s a step-by-step guide based on my experience that will help you become an expert in application security:
Start with a Solid Understanding of Cybersecurity Basics
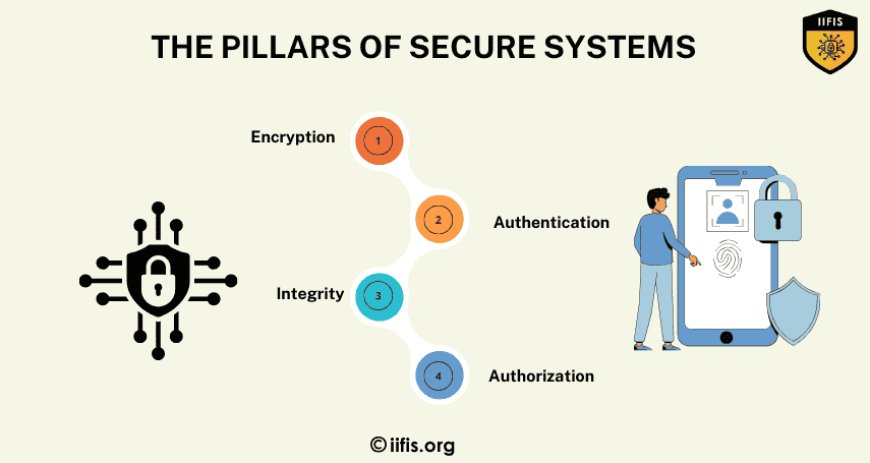
Before diving into application security specifically, you need a strong understanding of the broader cybersecurity landscape. Understanding concepts like encryption, threat modeling, risk management, and basic attack vectors is crucial.
-
Study Networking and Operating Systems: Learn about how networks function and how operating systems like Linux and Windows work. Application security often relies on understanding how data moves within these systems and how vulnerabilities in one area can impact the whole infrastructure.
-
Understand Security Terminology: Get comfortable with terms like confidentiality, integrity, and availability (CIA Triad), threat vectors, and risk management.
Develop Programming and Scripting Skills
As an application security expert, you need to think like a developer. You won’t be writing software every day, but you’ll need to understand how applications are built to identify vulnerabilities effectively.
-
Programming Languages: Learn languages such as Python, Java, JavaScript, C/C++, and Ruby. Understanding both server-side and client-side code will allow you to spot security flaws more easily.
-
Scripting: Scripting skills are essential for automating security tasks and testing. Learn scripting languages like Bash or PowerShell, which will be valuable for penetration testing, vulnerability scanning, and automating repetitive tasks.
Master the Web Technologies and Application Frameworks
Today, most applications are web-based, so it’s essential to understand how web applications work.
-
Web Technologies: Learn the fundamental web technologies such as HTML, CSS, JavaScript, and HTTP protocols. Web apps are built using these technologies, and understanding their workings is key to spotting vulnerabilities.
-
Frameworks and Libraries: Get to know popular web development frameworks like Angular, React, Django, and Ruby on Rails. Familiarity with these frameworks helps you identify framework-specific vulnerabilities like cross-site scripting (XSS) or SQL injection risks.
Learn Secure Coding Practices and Common Vulnerabilities
You need to understand how to prevent the most common vulnerabilities that plague applications.
-
OWASP Top 10: Start by studying the OWASP (Open Web Application Security Project) Top 10, which lists the most critical security risks for web applications. These include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and broken authentication.
-
Secure Development Lifecycle: Secure coding practices should be part of the development process from the beginning. Familiarize yourself with secure coding principles and how to integrate security checks at each phase of the development lifecycle.
Hands-on Practice with Security Tools
Theory is important, but practical experience is what will turn you into a true expert. There are various tools available that help identify vulnerabilities in applications.
-
Static Application Security Testing (SAST): Tools like Checkmarx and SonarQube scan your source code for vulnerabilities. This is crucial for identifying flaws in your code before deployment.
-
Dynamic Application Security Testing (DAST): Tools like Burp Suite, OWASP ZAP, and Acunetix scan running applications for security issues. This is essential for finding vulnerabilities in live environments.
-
Penetration Testing: Engage in hands-on penetration testing. Platforms like Hack The Box and TryHackMe are great for practicing your skills and learning how real-world exploits are performed.
Learn About Security Protocols and Authentication Mechanisms
As you develop your expertise, you will need to understand different authentication and security protocols that protect applications.
-
Authentication Methods: Learn about OAuth, OpenID, and other authentication protocols. Understanding how these protocols work is key to securing user data and preventing unauthorized access.
-
Encryption: Learn how encryption algorithms like AES, RSA, and hashing (SHA-256, bcrypt) work to secure data both in transit and at rest.
Study Threat Modeling and Risk Assessment
As an expert, one of your core responsibilities will be identifying, assessing, and mitigating risks in applications. Threat modeling helps you understand potential attack vectors in a system and plan how to defend against them.
-
Threat Modeling: Understand how to map out potential threats and vulnerabilities in an application. Use frameworks like STRIDE or PASTA to conduct risk assessments and identify possible security gaps.
-
Risk Mitigation: Focus on learning how to assess the severity of vulnerabilities and the business impact. This will help you prioritize which risks to address first.
Get Certified and Gain Formal Recognition
While hands-on experience is crucial, certifications add credibility and provide a structured learning path. Certifications are recognized across the industry and can significantly boost your career.
-
Certified Information Systems Security Professional (CISSP): While this is more general, it’s a great credential for anyone in cybersecurity, including application security.
-
Offensive Security Certified Professional (OSCP): This is a more hands-on, technical certification focused on penetration testing and offensive security.
-
Certified Web Application Security Expert (CWASE): This certification is designed for those who want to focus on securing web applications, including testing, securing code, and protecting against common vulnerabilities.
-
Certified Mobile Application Security Expert (CMASE): This certification focuses on the security of mobile applications, addressing specific vulnerabilities unique to mobile platforms and how to secure them effectively.
Stay Updated and Continuously Learn
Application security is a dynamic field. New vulnerabilities, threats, and tools emerge regularly, so staying up-to-date is vital.
-
Follow Industry Leaders: Follow security blogs, listen to podcasts, and participate in forums like Reddit’s r/netsec or Stack Overflow. This will help you keep track of new trends, tools, and tactics in application security.
-
Attend Security Conferences: Participate in conferences like Black Hat, DEF CON, or OWASP events to connect with other experts and learn about the latest security developments.
Build a Portfolio and Network
Building a strong network and portfolio is crucial for advancing your career.
-
Bug Bounty Programs: Platforms like HackerOne and Bugcrowd allow you to participate in bug bounty programs, where you can find and report vulnerabilities in real-world applications. This is great for building practical experience and recognition.
-
Contribute to Open Source Projects: Contribute to open-source security projects to show your expertise and build your reputation in the community.
As we know Becoming an application security expert requires a combination of strong foundational knowledge, hands-on experience, and a commitment to continuous learning. Begin by mastering cybersecurity principles and programming languages, then focus on understanding web technologies, secure coding practices, and common vulnerabilities like those outlined in the OWASP Top 10. Gaining proficiency with security tools such as SAST, DAST, and penetration testing platforms is essential. Earning industry-recognized certifications like CISSP, OSCP, and CWASE will enhance your credibility. Staying updated with evolving threats, contributing to open-source projects, and participating in bug bounty programs will help you refine your skills and establish your expertise in the field.























