Top Web Application Security Measures You Need
Implement encryption, strong authentication, regular updates, firewalls, and vulnerability testing to safeguard your web application from security threats and breaches

What is web application security?
When I first worked with web applications, I didn’t realize how vulnerable they could be until we faced a cyber attack. The breach threatened sensitive user data and disrupted our services, showing how easily things could go wrong. While we had some security measures, they weren't enough to prevent the attack in time.
That experience taught me that web application security is not just about functionality—it's about protecting data and user trust. We learned the importance of a multi-layered approach, including encryption, input validation, and regular testing, to defend against evolving threats and ensure the security of our applications.
Why is web application security important?
-
Protection of Sensitive Data: Web applications often handle sensitive personal or financial information. Any breach can lead to identity theft, fraud, or other serious consequences.
-
Compliance: Many industries require organizations to follow strict regulations for data protection. Implementing security measures ensures compliance with standards like GDPR, PCI-DSS, and HIPAA.
-
Business Continuity: A compromised web application can cause downtime, preventing customers from accessing your services and harming your business's operations.
-
Reputation Management: A security breach can tarnish your brand's reputation, leading to a loss of customer trust and damaging relationships with stakeholders.
-
Financial Loss: Data breaches often come with hefty penalties, legal fees, and lost revenue. Preventing attacks can save organizations from these financial burdens.
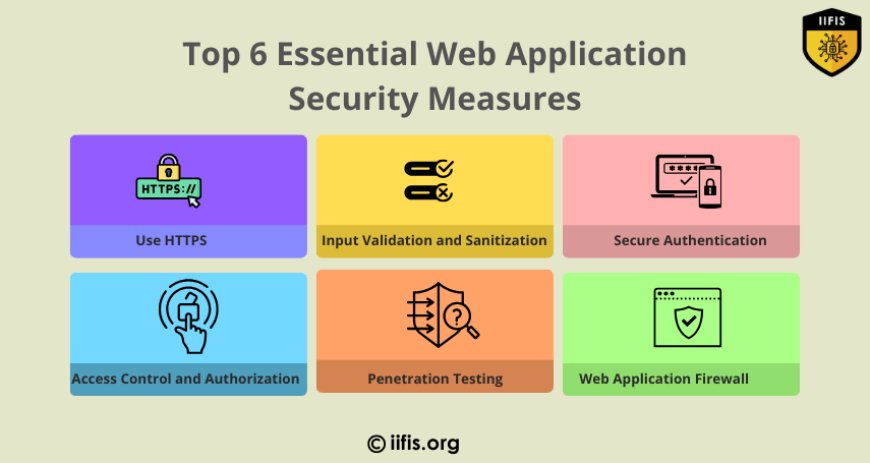
Top 6 Essential Web Application Security Measures
Now that we understand the significance of web application security, let’s dive into some of the most critical security measures you should implement to protect your web applications.
-
Use HTTPS (SSL/TLS Encryption)
HTTPS stands for HyperText Transfer Protocol Secure. It is an extension of HTTP that uses SSL/TLS (Secure Socket Layer/Transport Layer Security) protocols to encrypt the communication between a user's browser and your web server. This encryption ensures that data sent back and forth (like passwords, credit card numbers, or personal information) cannot be intercepted or tampered with by unauthorized parties.
Why it’s needed: Using HTTPS is critical because it protects sensitive data from being exposed to cybercriminals through man-in-the-middle attacks. Without HTTPS, all the data sent between the user and the server is transmitted in plain text, making it vulnerable to eavesdropping.
Key benefits:
-
Secure communication and data transfer
-
Protects against interception of sensitive information
-
Enhances trust among users (browser shows a padlock icon when HTTPS is used)
-
Improves SEO rankings, as Google favours HTTPS websites
-
Input Validation and Sanitization
Input validation is the process of ensuring that user inputs are correct and follow the expected format. Input sanitization, on the other hand, involves cleaning up or filtering the inputs to prevent malicious code from being executed on the server.
Why it’s needed: Web applications are often targets of attacks like SQL injection, cross-site scripting (XSS), and command injection. If user inputs are not validated or sanitized, attackers could inject malicious code that compromises the application or its database.
Key benefits:
-
Prevents attacks like SQL injection and XSS
-
Ensures the integrity of the data entered into the system
-
Reduces the chances of malicious users exploiting input fields
-
Secure Authentication
Secure authentication involves verifying a user’s identity before granting access to the web application. This typically includes usernames, passwords, and sometimes additional factors like two-factor authentication (2FA) or biometric verification.
Why it’s needed: Weak or poorly managed authentication mechanisms are often exploited by attackers to gain unauthorized access to sensitive data. Implementing secure authentication ensures that only legitimate users can access protected resources.
Key benefits:
-
Prevents unauthorized access
-
Enhances user privacy and data security
-
Reduces the risk of brute-force and credential-stuffing attacks
-
2FA adds a layer of security
-
Access Control and Authorization
Access control refers to the practice of granting or restricting access to resources based on the user's role or identity. Authorization ensures that users can only access resources they are permitted to, based on their role (admin, user, guest, etc.).
Why it’s needed: Poor access control mechanisms can lead to privilege escalation, where an attacker gains higher levels of access than they should have, potentially leading to data leaks, system damage, or unauthorized changes.
Key benefits:
-
Ensures users only access what they're authorized to
-
Prevents unauthorized actions from taking place
-
Reduces the risk of a compromised account leading to a full system breach
-
Regular Security Audits and Penetration Testing
Security audits and penetration testing involve reviewing your web application for vulnerabilities and attempting to exploit them (ethically) to identify weaknesses. These tests can be performed manually or with automated tools.
Why it’s needed: Even with the best security measures in place, new vulnerabilities emerge regularly. Security audits and penetration testing help identify these weaknesses before an attacker can exploit them.
Key benefits:
-
Identifies vulnerabilities before attackers can exploit them
-
Helps improve overall system security and integrity
-
Provides a comprehensive assessment of the application’s defenses
-
Keeps the application compliant with industry standards
-
Web Application Firewall (WAF)
A Web Application Firewall (WAF) is a security system that monitors and filters incoming traffic to your web application. It identifies and blocks malicious requests, such as SQL injections, cross-site scripting (XSS), and other common threats.
Why it’s needed: Web applications are constantly under attack from various sources. A WAF acts as a barrier between the web server and the internet, blocking potentially malicious traffic before it can reach the application.
Key benefits:
-
Protects the web application from common attack vectors
-
Helps prevent data breaches by blocking malicious requests
-
Provides an additional layer of security without altering the application code
-
Can be customized to block specific threats or vulnerabilities
Purse Certifications in Web Application and Mobile Security
Pursuing certifications in web and mobile application security is a great way to boost your career and stay updated on the latest security practices. For web applications, certifications like Certified Web Application Security Expert (CWASE) provide key skills in penetration testing and secure coding.
For mobile security, certifications such as Certified Mobile Application Security Expert (CMASE) focus on securing mobile applications against unique threats. These certifications not only enhance your professional credibility but also equip you with the tools to tackle evolving security challenges effectively.
Web application security is crucial for protecting sensitive data, ensuring compliance, and maintaining business continuity. Implementing essential security measures like HTTPS, input validation, and secure authentication helps defend against evolving threats. Pursuing certifications in web and mobile security further strengthens your ability to safeguard applications effectively.























