A Beginner’s Guide to Penetration Testing
Learn the fundamentals of penetration testing with this beginner’s guide. Explore tools, methods, and tips to start your ethical hacking journey confidently.

As a certified penetration tester, I specialize in identifying and exploiting vulnerabilities in systems, networks, and applications to strengthen cybersecurity defenses. My work involves ethical hacking techniques, comprehensive assessments, and detailed reporting to help organizations stay secure. With a deep understanding of attack vectors and defense strategies, I ensure systems are resilient against real-world threats.
What Is Penetration Testing?
Penetration Testing, also known as ethical hacking, is a simulated cyberattack performed by security professionals to identify and exploit vulnerabilities in a system, network, or application. The goal is to uncover security weaknesses before security hackers can exploit them. It helps organizations assess their security posture, test defense mechanisms, and improve their overall cybersecurity strategy.
Why Is Penetration Testing Important?
Organizations face constant threats from cybercriminals. Every day, systems are scanned for vulnerabilities. Without penetration testing, these weaknesses can remain hidden—until it's too late.
Here’s why penetration testing is essential:
-
Identify security gaps before attackers do
-
Meet compliance standards (e.g., GDPR, HIPAA, PCI-DSS)
-
Test your incident response readiness
-
Build trust by demonstrating strong security practices
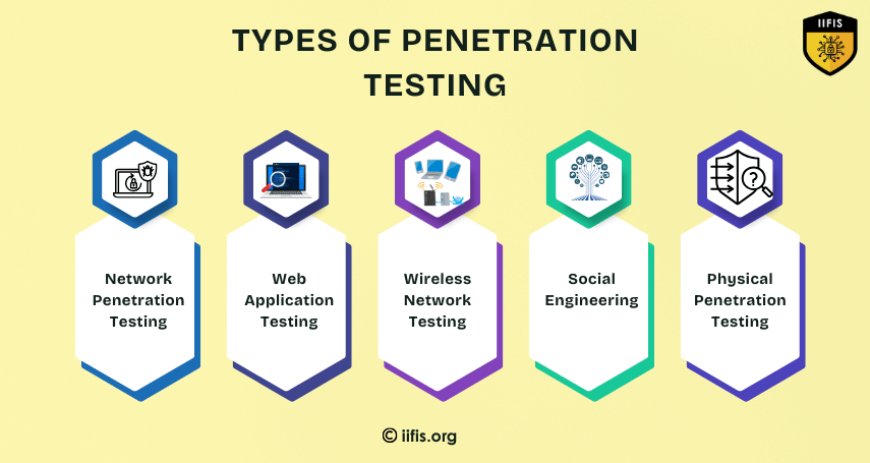
Types of Penetration Testing
Penetration testing in cybersecurity varies based on the target and objectives. Each type helps uncover different aspects of an organization's security posture:
-
Network Penetration Testing: Evaluates internal and external network infrastructure for vulnerabilities like open ports, misconfigured firewalls, and insecure protocols.
-
Web Application Testing: Assesses websites and applications for flaws such as SQL injection, cross-site scripting (XSS), broken authentication, and more.
-
Wireless Network Testing: Examines Wi-Fi networks for weak encryption, unauthorized access points, and poor access controls.
-
Social Engineering: Tests human factors by simulating phishing emails, phone pretexting, or baiting attacks to assess employee awareness and training.
-
Physical Penetration Testing: Involves attempting to gain unauthorized physical access to buildings or sensitive areas to test locks, badge systems, and security personnel.
The Penetration Testing Process
-
Planning & Reconnaissance
Define scope, objectives, and rules of engagement. Gather intelligence (e.g., domain info, IPs, emails) to identify potential attack vectors. -
Scanning & Enumeration
Use tools to scan systems for open ports, services, and vulnerabilities. This helps map the network and identify targets. -
Gaining Access
Attempt to exploit discovered vulnerabilities using techniques like SQL injection, buffer overflow, or password cracking. -
Maintaining Access
Try to establish a persistent presence to see if long-term access can be maintained, mimicking advanced threat actors. -
Analysis & Reporting
Document findings, including vulnerabilities, exploitation methods, and suggested remediation steps. Deliver to stakeholders. -
Remediation & Retesting
After fixes are applied, retesting ensures the vulnerabilities are properly resolved and no new issues have been introduced.
Tools Used in Penetration Testing
-
Reconnaissance & Information Gathering
-
Nmap – Network mapping and port scanning
-
Maltego—OSINT and relationship mapping
-
The Harvester – Collects emails, subdomains, and public data.
-
Scanning & Vulnerability Assessment
-
Nessus—Vulnerability scanner
-
OpenVAS—an open-source alternative for vulnerability scanning
-
Nikto – Web server scanner
-
Exploitation
-
Metasploit Framework—A Powerful platform for developing and executing exploits
-
SQLmap—Automated SQL injection tool
-
Hydra—brute-force login tool for various protocols
-
Post-Exploitation
-
Mimikatz—Extracts credentials from Windows systems
-
Empire – PowerShell-based post-exploitation agent
-
BloodHound – Analyzes Active Directory for privilege escalation paths
-
Wireless Testing
-
Aircrack-ng—cracking Wi-Fi passwords and analyzing wireless traffic
-
Kismet—Wireless network detector and sniffer
-
Social Engineering
-
SET (Social-Engineer Toolkit)—Simulates phishing and other social engineering attacks
-
Reporting
-
Dradis – Collaborative reporting and information sharing
-
Faraday—a centralized platform for managing test results
Skills Needed to Become a Penetration Tester
Penetration testing is both an art and a science. It requires a blend of technical skills, problem-solving abilities, and a curious mindset.
To start, a beginner should focus on
-
Networking Knowledge: Understanding of protocols (TCP/IP, DNS, HTTP), firewalls, and network architectures.
-
Operating System Expertise: Proficiency in Linux and Windows environments, including command-line usage and system internals.
-
Programming & Scripting: Knowledge of languages like Python, Bash, or PowerShell for automating tasks and writing custom tools.
-
Web Application Security: Understanding of common vulnerabilities (e.g., XSS, SQLi, CSRF) and how web technologies work.
-
Vulnerability Assessment & Exploitation: Skill in using tools and manual techniques to find and exploit weaknesses.
-
Social Engineering Awareness: Ability to craft phishing campaigns or perform physical security tests as part of human-layer testing.
-
Knowledge of Security Standards: Familiarity with OWASP Top 10, MITRE ATT&CK, and compliance frameworks like PCI-DSS and ISO 27001.
-
Analytical & Problem-Solving Skills: Strong critical thinking to assess complex systems and uncover subtle security flaws.
-
Report Writing & Communication: Ability to document findings, explain technical issues to non-technical stakeholders, and recommend fixes.
How to Get Started with Penetration Testing
If you’re just getting started with penetration testing, here are some steps to guide your journey:
-
Start Learning Basics: There are many online courses and tutorials on cybersecurity and pen testing.
-
Set Up a Lab: Create a virtual environment using tools like VirtualBox or VMware to practice safely.
-
Join Communities: Get involved in forums, Discord servers, or Reddit groups dedicated to cybersecurity.
-
Participate in CTFs (Capture The Flag challenges): These gamified hacking contests help sharpen your skills.
-
Earn a Certification: Once you're confident, getting certified by IIFIS can boost your credibility.
Penetration testing is an exciting, rewarding, and essential aspect of modern cybersecurity. It helps businesses stay ahead of threats and empowers individuals with the skills to protect systems and data. For beginners, the journey may seem overwhelming, but with curiosity, dedication, and the right guidance, you can build a solid foundation.
























