Understanding Zero Trust Architecture in Network Security
Zero Trust Architecture in network security ensures no user or device is trusted by default. It enforces strict identity verification and continuous monitoring for enhanced security.
As a certified network security expert, I have observed how the digital landscape is constantly evolving, with cyber threats becoming increasingly advanced and complex. Traditional security models, such as perimeter-based defense, are no longer sufficient. Attackers can now exploit vulnerabilities in devices or users already inside the network, bypassing external defenses.
To counter these advanced threats, many organizations are turning to Zero Trust Architecture (ZTA) as a core security model. This approach challenges the old "trust but verify" model, assuming that every user, device, and application - whether inside or outside the network - could be compromised.
What is Zero Trust Architecture?
Zero Trust Architecture is a security model based on the principle of "never trust, always verify." It treats every user, device, and application as potentially compromised, regardless of location, requiring continuous authentication before granting access. Instead of relying on a single perimeter, Zero Trust secures individual resources and network segments, minimizing the risk of lateral movement for attackers, even if they breach part of the network.
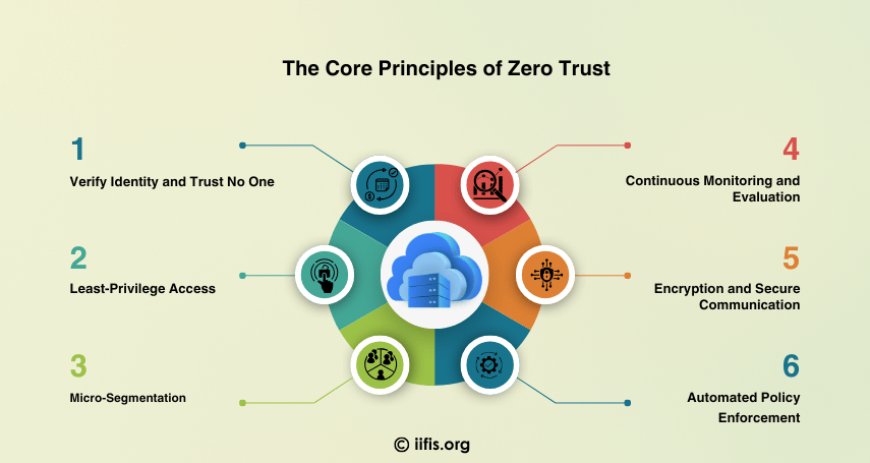
The Core Principles of Zero Trust
Zero Trust relies on several core principles to enhance network security:
-
Verify Identity and Trust No One: Every user, device, and application must prove their identity before accessing resources. This is achieved through strong authentication methods, such as multi-factor authentication (MFA), device certificates, and identity and access management (IAM) solutions.
-
Least-Privilege Access: Zero Trust advocates for the principle of least privilege, where users and devices are granted only the minimum access necessary to perform their job. This minimizes the potential damage if an attacker gains access to a system, as they are limited in what they can do.
-
Micro-Segmentation: Instead of relying on a single perimeter defense, Zero Trust utilizes micro-segmentation to divide the network into smaller, isolated zones. This ensures that even if an attacker penetrates one segment, they cannot move laterally through the entire network without being detected and blocked.
-
Continuous Monitoring and Evaluation: Zero Trust emphasizes continuous monitoring of users, devices, and network traffic. Even after an entity is granted access, its behavior is constantly evaluated to detect any anomalous or suspicious activities. This helps in quickly identifying and mitigating any breaches or attacks.
-
Encryption and Secure Communication: All data in transit and at rest should be encrypted. Zero Trust requires encryption to protect sensitive data and ensure that unauthorized entities cannot intercept or manipulate it.
-
Automated Policy Enforcement: Zero Trust relies on automated systems to enforce security policies. By using machine learning and AI, these systems can assess risk, enforce policies dynamically, and respond to security incidents in real-time
Why Zero Trust is Necessary
Traditional security models focused on creating a strong perimeter defense, assuming that threats mostly came from external sources. However, as technology and work habits have changed, this approach has become outdated. Some of the primary reasons why Zero Trust has become essential include:
-
The Rise of Remote Work: With more employees working from home or other remote locations, the perimeter-based security model no longer applies. Users and devices are connecting from various locations and networks, making it harder to protect against internal and external threats using traditional firewalls and VPNs.
-
Cloud Adoption: As more businesses migrate to cloud services, the traditional network perimeter becomes less relevant. Data and applications are no longer confined to on-premises infrastructure. Zero Trust provides a framework that adapts to cloud environments, securing data wherever it resides.
-
Insider Threats: Insider threats—whether from malicious actors or unintentional mistakes—pose a significant risk to organizations. Zero Trust assumes that even insiders can be compromised, and therefore, no one should have implicit trust.
-
Advanced Persistent Threats (APTs): APTs are often highly sophisticated and can evade traditional security measures for long periods. Zero Trust reduces the risk of lateral movement by limiting access based on continuous verification and segmentation.
-
Protecting Sensitive Data: As organizations handle more sensitive and regulated data, ensuring its security becomes paramount. Zero Trust’s fine-grained access control and encryption ensure that sensitive data is only accessed by authorized individuals, reducing the risk of data breaches.
How to Implement Zero Trust Architecture
Implementing Zero Trust requires a strategic approach. Here are the key steps involved:
-
Understand the Organization’s Assets: The first step is identifying all assets that need protection, including users, devices, applications, data, and network segments. You’ll need to understand where your sensitive data resides and which systems are most critical.
-
Define and Classify Access: After identifying the critical assets, organizations should define policies that govern who can access what resources and under what conditions. This involves setting up user and device authentication mechanisms and classifying resources based on their sensitivity.
-
Implement Identity and Access Management (IAM): IAM solutions are crucial for managing who has access to what resources. Implement multi-factor authentication (MFA), single sign-on (SSO), and identity federation to ensure that only authorized users and devices can access network resources.
-
Use Micro-Segmentation: Divide the network into smaller segments and apply security policies to each segment. This limits the movement of attackers if they gain access to one part of the network.
-
Monitor and Analyze Traffic Continuously: Continuous monitoring is essential for detecting and responding to threats. Use security information and event management (SIEM) systems to track user behavior, network traffic, and access patterns.
-
Automate Response and Policy Enforcement: Automating security policies and responses helps reduce the burden on security teams and ensures that security measures are always applied consistently. Implement tools that use AI and machine learning to adapt to evolving threats.
-
Train Employees and Partners: Zero Trust relies on both technology and human behavior. Regularly train employees on security best practices and the importance of Zero Trust policies to ensure full adoption.
The Benefits of Zero Trust Architecture
Zero Trust offers a range of benefits for organizations looking to improve their network security:
-
Reduced Attack Surface: By restricting access based on continuous verification and minimizing unnecessary privileges, Zero Trust reduces the potential attack surface for cybercriminals.
-
Enhanced Data Protection: With encryption, micro-segmentation, and least-privilege access, sensitive data is better protected from unauthorized access and breaches.
-
Stronger Defense Against Insider Threats: Zero Trust assumes that threats could come from both internal and external sources, allowing organizations to prevent unauthorized access even from trusted insiders.
-
Adaptability to Modern IT Environments: As organizations move to cloud-based environments, Zero Trust provides the necessary framework to secure resources regardless of location.
-
Compliance with Regulations: Zero Trust’s approach to data security, privacy, and governance can help organizations meet regulatory requirements and safeguard sensitive data.
Zero Trust Architecture is essential for modern network security, focusing on continuous verification, least-privilege access, and micro-segmentation to protect against evolving threats. Traditional perimeter defenses are no longer enough. Zero Trust offers a flexible framework for securing digital assets, especially in remote work and cloud environments. A network security certification can help professionals master these critical concepts.
























