Network Security Best Practices and Case Studies
Explore essential network security practices and real-world case studies to safeguard your digital infrastructure. Learn from industry experts.

Network security best practices are critical for businesses as they help protect sensitive data and counteract cyber-attacks. Businesses can reduce their risk of financial losses, reputational damage, and data mistakes by implementing these procedures.
To begin with, strong network security protocols maintain data confidentiality. This implies that sensitive data, like bank records, customer information, and intellectual property, can only be accessed by those who are allowed. Businesses may preserve confidence with their partners and customers by keeping this information private, which is important to long-term success.
The confidentiality of data is improved by network security best practices. This involves protecting against improper changes or modifications for data to be true to form. Businesses may avoid mistakes, mistakes, and losses resulting from modification or hacking by upholding data security.
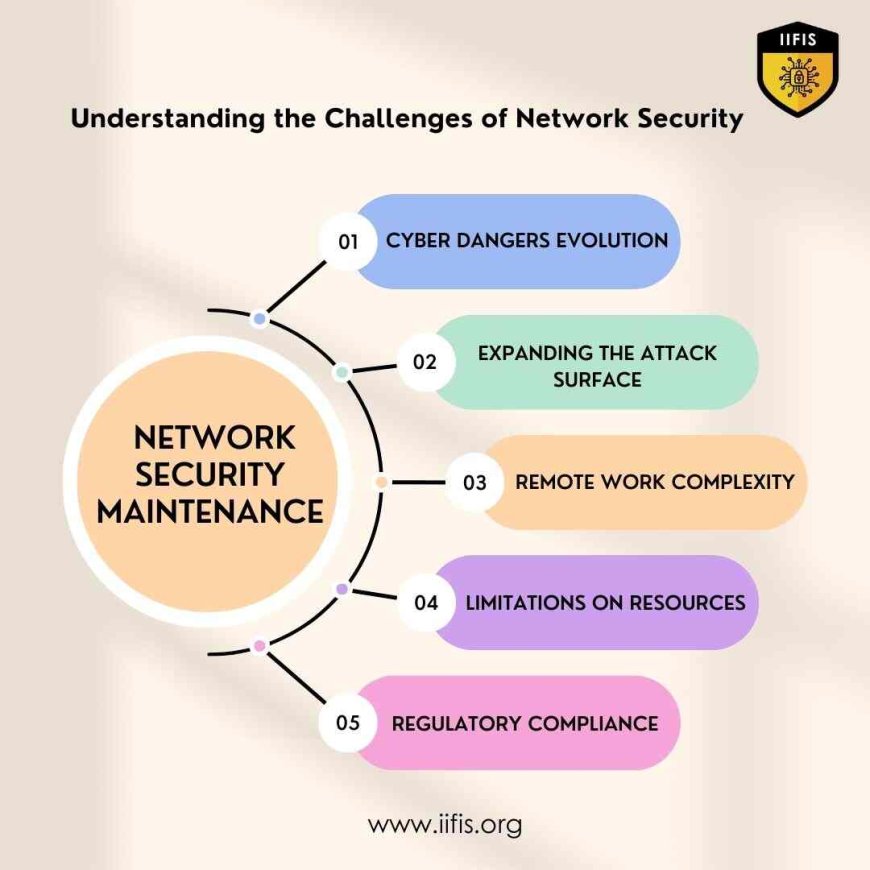
Understanding the Challenges of Network Security Maintenance
Network security is more important than ever in the current digital environment. It is not without difficulties, though. Now let's explore the details:
-
Cyber dangers Evolution :
-
The ever-changing strategies of hackers present a challenge for companies to stay up to currently available.
-
Cyber dangers are always changing taking advantage of loopholes in networks and systems.
-
Expanding the Attack Surface:
-
The attack surface grows as a result of the Internet of Things (IoT) broad availability.
-
Network security management becomes more difficult as a result of the ability of cyberattacks to enter through any connected device.
-
Remote Work Complexity:
-
Employees can now access company networks from several devices and locations thanks to the advent of work-from-home.
-
New security dangers, such as deploying personal devices and unprotected Wi-Fi networks, are brought forth by this decentralization.
-
Limitations on Resources:
-
Significant resources are needed for maintaining network security, including highly qualified staff, advanced technology, and continual training.
-
Many organizations find it difficult to devote the necessary funds and resources to effectively manage these demands.
-
Regulatory Compliance:
-
Following rules and industry guidelines raises the standard for network security protections.
-
If these conditions are not met, there may be serious repercussions, such as fines and damages to the organization's reputation.
Companies need to understand these problems to create efficacious strategies for upholding network security. Businesses may better defend their networks and sensitive data from cyber threats by taking on these issues directly.
What are the best practices for improving network security?
Improving network security is critical for protecting private information and avoiding online dangers. The following are recommended procedures to improve network security
Regular Software Updates: Make sure that the most recent security updates are applied to all software, including operating systems, security software, and applications. This lessens the possibility that hackers will take advantage of the weaknesses and helps to fix them.
Strong Password Guidelines: Develop strong password rules enabling employees to use unique passwords that they update regularly. Promote the usage of passwords based on passwords, which are simple to remember but challenging for hackers to crack.
Multi-Factor Authentication (MFA): Turn on multi-factor authentication (MFA) to increase security. Usually, this means asking users to identify themself using two or more different methods, like a password and a one-time code sent to their mobile device.
Network Segmentation: Divide your network into several zones or subnetworks to prevent cyberattacks from growing. By doing this, safety risks are lessened and hackers are kept out of important network locations.
firewall Settings: Firewalls can be set up to filter incoming and outgoing traffic according to preset rules. This helps to prevent software from passing through the network and blocking unwanted access.
Regular Security Audits: Perform regular security audits to find holes and weak points in your network infrastructure. Penetration testing, vulnerability scanning, and security evaluations by outside experts are examples of technology.
Employee Training and Awareness: Employees should receive thorough training on security best practices, including how to identify phishing emails, keep clear of social engineering scams, and report problematic activities. Raising staff awareness is useful in avoiding human error-related safety issues.
Data Privacy: To avoid unwanted access, protect sensitive data while it's in movement and at repose. To secure data while it's in movement, use encryption technologies like SSL/TLS, and for data that's stored on servers or other devices, use encryption methods.
Regular Backup and Disaster Recovery: Implement frequent backup methods to ensure that important data is properly backed up and can be recovered in the case of a security attack or data loss. Create a thorough disaster recovery plan to reduce lost time and lessen the effects of online dangers.
Importance of Network Security Best Practices
The importance of network security is unexpected in the online world for several reasons.
Protecting Private Information:
Financial records and personal information are protected by network security against cyber threats including viruses and fake emails as well as illegal access.
Keeping the Business Alive:
It makes sure business activities by reducing downtime and problems restored by security events.
Enabling Compliance with Regulations:
Strong network security controls assist in maintaining stakeholders' trust, avoiding legal issues, and complying with regulations.
Maintaining Reputation:
An organization's reputation is improved by displaying a dedication to secrecy and data security.
Protecting Remote Access:
It is important for protecting remote access, particularly in the increasingly remote workplace.
Stopping Data Theft:
Putting security measures in place, such as firewalls and encoding, helps stop data thefts and the damage they explain.
Overall Importance:
Network security is important for protecting digital information, upholding company values, and maintaining trust in today's interconnected world.
Network security best practices are necessary for companies to safeguard sensitive information, fend off online attacks, and keep their partners' and consumers' trust. Organizations may greatly improve their network security posture by putting strong network security protocols into place. These protocols include frequent software updates, strong password policies, multi-factor authentication, network segmentation, firewall settings, regular security audits, employee training, data encryption, and regular backup and disaster recovery methods. Developing effective strategies to maintain network security requires an understanding of the challenges associated with it, including evolving cyber threats, the expanding attack surface due to the Internet of Things (IoT), the difficulties of remote work, resource limitations, and compliance with regulations.























