Basic Cybersecurity Tips for Everyone
Learn essential cybersecurity tips to protect yourself online. Discover simple, practical steps to safeguard your data, prevent cyber threats, and stay safe in the digital world.

Cybersecurity is the practice of protecting systems, networks, and data from digital threats such as malware, hacking, and unauthorized access. It involves a range of measures, including network defences, application security, data protection, and operational policies to ensure that information remains confidential, integral, and available. Cybersecurity includes educating users about potential threats and implementing disaster recovery plans to maintain operations in the event of a cyber incident. As technology evolves, so do the methods used by attackers, making robust cybersecurity essential for safeguarding digital assets and maintaining trust.
What is cybersecurity?
Cybersecurity is all about keeping your computers, networks, and data safe from online threats and attacks. It is a digital security guard that shields you from malware, ransomware, and phishing scams. It uses a mix of tools like encryption, firewalls, and secure coding to keep things safe. Plus, it involves teaching people how to spot and handle potential threats. And if something does go wrong, cybersecurity helps make sure you can bounce back and keep things running smoothly.
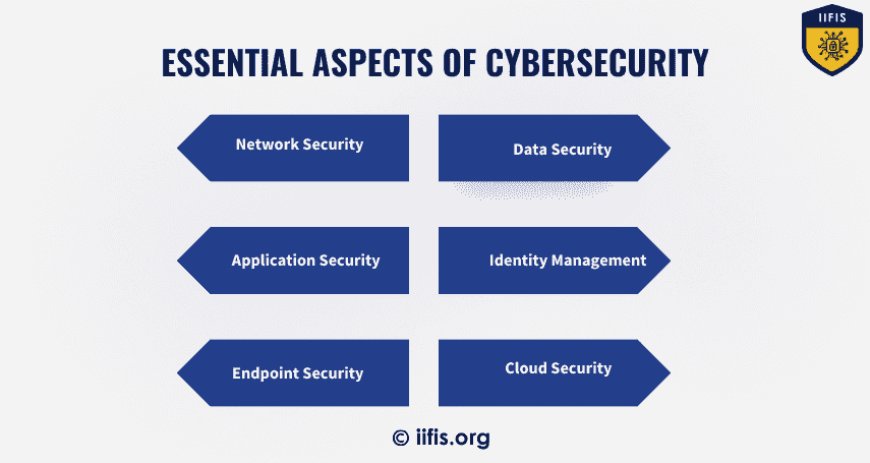
Cybersecurity covers a lot of ground, including:
-
Network Security: Keeping networks safe from intruders and malicious software, whether they're targeting you specifically or just taking advantage of vulnerabilities.
-
Application Security: Making sure that software and devices are fortified against threats, as a weak app could let attackers access sensitive data.
-
Endpoint Security: Securing devices like computers and smartphones, which are often the entry points for cyber attacks.
-
Data Security: Protecting sensitive information from being accessed, stolen, or exposed by unauthorized parties.
-
Identity Management: Ensuring that only the right people have access to certain information and resources.
-
Cloud Security: Safeguarding data and services that are stored and accessed through the cloud from cyber threats.
Types of cybersecurity threats
Cybersecurity threats come in various forms, each with its own methods and goals. Here are some common types:
-
Malware: malicious software designed to harm systems. This includes viruses, worms, and trojans, which can steal data, damage files, or create backdoors for further attacks.
-
Ransomware: A type of malware that secures a victim's data and demands a ransom for the decryption key. It's often delivered through emails or compromised websites.
-
Phishing: false attempts to trick individuals into providing sensitive information, like passwords or credit card numbers, often through fake emails or websites that look legitimate.
-
Man-in-the-Middle attacks: occur when an attacker intercepts and alters communications between two parties without their knowledge. This can lead to data theft or manipulation.
-
Denial of Service (DoS) Attacks: a system, network, or website with traffic, making it unavailable to users. A Distributed Denial of Service (DDoS) attack amplifies this by using multiple sources.
-
SQL Injection: takes advantage of weak points in a website's database by injecting malicious SQL code, allowing attackers to access, modify, or delete data.
-
Zero-day exploits: Attacks that target previously unknown vulnerabilities in software or hardware before developers have had a chance to address the issue.
-
Insider Threats: risks posed by individuals within an organization, such as employees or contractors, who misuse their access to steal data or cause harm.
-
Social engineering: manipulating people into divulging confidential information or performing actions that compromise security, often through deception or psychological manipulation.
-
Advanced Persistent Threats (APTs): prolonged and targeted cyberattacks where an attacker gains unauthorized access to a network and remains undetected for an extended period or data theft.
Importance of Cybersecurity
Cybersecurity is crucial for several reasons:
-
Protects sensitive data: It safeguards personal, financial, and business information from theft or exposure, which helps maintain privacy and trust.
-
Prevents Financial Loss: cybersecurity measures help prevent costly breaches, fraud, and theft, which can have significant financial implications for individuals and businesses.
-
Ensures Business Continuity: By defending against cyberattacks and data breaches, cybersecurity helps keep operations running smoothly and minimizes downtime, which is key for maintaining productivity and service delivery.
-
Maintains Reputation: A strong cybersecurity position helps build and maintain trust with customers, clients, and partners. A security breach can damage a company's reputation and lead to a loss of customer confidence.
-
Compliance with Regulations: Many industries are subject to regulations requiring data protection measures. Cybersecurity helps ensure compliance with these laws and avoid legal penalties.
-
Protects Against Evolving Threats: As technology and cyber threats evolve, robust cybersecurity helps stay ahead of emerging risks and weaknesses, ensuring ongoing protection.
-
Secures Innovation: With the rise of new technologies like IoT and cloud computing, Cybersecurity is essential to protect these innovations from being exploited and to ensure they can be used safely and effectively.
Cybersecurity Best Practices
-
Use Strong, Unique Passwords: Create strong passwords that combine letters, numbers, and symbols. Avoid reusing passwords across different accounts.
-
Enable Multi-Factor Authentication (MFA): Add an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
-
Keep Software and Systems Updated: Regularly update your operating system, applications, and antivirus software to protect against the latest threats and vulnerabilities.
-
Install and Maintain Antivirus Software: Use reputable antivirus programs to detect and remove malware and other security threats.
-
Backup Important Data: Regularly back up your data to secure locations, such as external drives or cloud storage, to ensure you can recover it in case of a cyber incident.
-
Be cautious with emails and links: Avoid clicking on suspicious links or downloading attachments from unknown sources. Verify the authenticity of emails before responding or taking action.
-
Secure Your Network: Use strong, unique passwords for your Wi-Fi network, enable network encryption (like WPA3), and consider using a Virtual Private Network (VPN) for added security.
-
Educate yourself and others: Stay informed about current cybersecurity threats and best practices. Educate colleagues, friends, and family members about safe online behaviors.
-
Monitor Accounts and Systems: Regularly review your financial statements, system logs, and security alerts for any unusual activity or signs of a breach.
-
Implement Access Controls: Limit access to sensitive information and systems to only those who need it. Use role-based access controls to ensure appropriate permissions
Developing trends in cybersecurity
1. Artificial Intelligence (AI) and Machine Learning (ML)
a. Enhanced threat detection and response
AI and ML are transforming threat detection and response capabilities. These technologies can analyze vast amounts of data, identify patterns, and detect anomalies that might indicate a security threat.
-
Behavioral Analysis: AI can monitor user behavior to detect deviations from normal patterns, which may suggest a compromised account or insider threat.
-
Automated Incident Response: Machine learning algorithms can automate responses to detected threats, such as isolating affected systems or blocking malicious traffic.
b. Predictive Analytics
AI and ML can also predict potential threats by analyzing historical data and identifying emerging trends. This proactive approach helps organizations anticipate and mitigate risks before they materialize.
Zero Trust Architecture
a. Principle of Least Privilege
Zero Trust is a security model based on the principle of "never trust, always verify." It assumes that threats could be both external and internal, and therefore, no entity—whether inside or outside the network—should be trusted by default. Key components include:
-
Micro-Segmentation: Dividing the network into smaller, isolated segments to limit the spread of potential threats.
-
Continuous Authentication: Verifying the identity and access rights of users and devices continuously rather than relying on one-time authentication.
b. least privilege access
Access to resources is granted based on the principle of least privilege, meaning users and systems are given only the permissions necessary to perform their tasks. This limits the potential impact of a compromised account or system.
Extended Detection and Response (XDR)
a. Integrated Security Solutions
XDR is an integrated approach to threat detection and response that combines data from multiple security products into a unified platform. It aims to provide a holistic view of an organization’s security posture by:
-
Centralized Monitoring: collecting and analyzing data from various sources, including endpoints, networks, and cloud environments.
-
Unified Response: Coordinating responses to threats across different security layers to improve efficiency and effectiveness.
b. Enhanced Visibility
XDR solutions offer enhanced visibility into security incidents, helping organizations quickly identify and address threats. This comprehensive view helps in reducing the time to detect and respond to incidents.
Cloud Security
a. Cloud-Native Security Tools
As more organizations migrate to cloud environments, there is a growing need for cloud-native security solutions. These tools are designed specifically to protect cloud-based assets and services. Examples include:
-
Cloud Access Security Brokers (CASBs): Provide visibility and control over cloud services and data.
-
Cloud Security Posture Management (CSPM): Tools that help manage and enforce security configurations and policies in cloud environments.
b. Securing multi-cloud and hybrid environments
Organizations often use multiple cloud providers and combine cloud resources with on-premises infrastructure. Securing these multi-cloud and hybrid environments requires:
-
Consistent Security Policies: Implementing uniform security policies across different cloud environments.
-
Integration with Existing Security Tools: Ensuring compatibility and integration with existing security solutions.
Privacy Enhancing Technologies (PETs)
a. Data Anonymization and Masking
PETs are designed to protect personal and sensitive information while enabling its use for analytics and other purposes. Techniques include:
-
Data anonymization: removing personally identifiable information (PII) from datasets to prevent the identification of individuals.
-
Data Masking: Replacing sensitive data with fictional or scrambled data to protect it during processing or testing.
b. Privacy-Enhancing Computation
Emerging technologies such as homomorphic encryption and secure multi-party computation allow data to be processed and analyzed without exposing its contents. This helps protect data privacy while still enabling valuable insights.
Quantum Computing and Cryptography
a. Quantum-Resistant Cryptography
Quantum computing poses a potential threat to traditional encryption methods. To address this, researchers are developing quantum-resistant cryptographic algorithms that are designed to be secure against the computational power of quantum computers.
b. Quantum Key Distribution
Quantum key distribution (QKD) uses principles of quantum mechanics to securely exchange encryption keys. This method ensures that any eavesdropping on the key exchange can be detected, enhancing the security of encrypted communications.
Security Automation and Orchestration
a. Automated Security Operations
Automation is increasingly used to streamline security operations, such as:
-
Automated threat detection: using algorithms and scripts to identify and respond to threats without human intervention.
-
Security Orchestration: Coordinating and integrating various security tools and processes to improve overall efficiency and effectiveness.
b. Reduced Time-to-Respond
Automation helps reduce the time it takes to detect, analyze, and respond to security incidents. This is crucial for minimizing the impact of cyberattacks and improving overall security posture.
Privacy Regulations and Compliance
a. Increasing regulatory requirements
As privacy concerns grow, governments and regulatory bodies are implementing stricter data protection laws. Organizations must comply with regulations such as:
-
General Data Protection Regulation (GDPR): A comprehensive data protection regulation in the European Union.
-
California Consumer Privacy Act (CCPA): A California law that provides consumers with greater control over their personal data.
b. Compliance Automation
Organizations are using automated tools to manage and demonstrate compliance with privacy regulations. These tools help streamline compliance processes, track regulatory changes, and generate necessary reports.
Human Factor and Security Awareness
a. Enhancing security training
Despite technological advancements, human factors remain a significant security risk. Organizations are investing in:
-
Security Awareness Programs: Training employees to recognize and respond to phishing attacks, social engineering, and other security threats.
-
Simulated Attacks: Conducting simulated phishing and social engineering attacks to test and improve employee awareness.
b. Behavioral Analytics
Using behavioral analytics to monitor employee activities and identify unusual patterns can help detect potential insider threats and mitigate risks associated with human error.
Internet of Things (IoT) Security
a. Securing IoT Devices
The proliferation of IoT devices introduces new security challenges. Key considerations include:
-
Device Authentication: ensuring that IoT devices are securely authenticated before being allowed to connect to networks.
-
Data Encryption: Encrypting data transmitted by IoT devices to protect it from interception and tampering.
b. Network Segmentation
Segmenting networks to isolate IoT devices from critical systems helps prevent the spread of potential threats and enhances overall security.
Cybersecurity is essential for safeguarding our digital world from a wide range of threats, including malware, phishing, and data breaches. By implementing robust security measures, such as strong passwords, multi-factor authentication, and regular system updates, individuals and organizations can protect sensitive information and ensure business continuity. As cyber threats evolve, staying informed and adopting best practices is crucial. Additionally, the International Information Systems Security Certification Consortium (IIFIS) provides valuable certifications that validate expertise and commitment to cybersecurity, helping professionals and organizations stay ahead in the ever-changing landscape of digital security.
























