Application Security in Cyber Security: Key Threats & Defenses
Learn major app security threats & best defenses to safeguard against cyber risks like injection attacks, zero-days, and data breaches.

As cyber threats become more advanced, keeping applications secure is more important than ever. Hackers look for weaknesses in software to access data, disrupt operations, and cause financial harm. Whether you work in development, IT, or run a business, knowing the risks and how to protect applications is essential.
Understanding Application Security in Cyber Security
Before going into threats and solutions, let’s clarify what application security in cyber security means. Application security is a set of strategies and measures designed to protect software applications from security vulnerabilities throughout their lifecycle. It ensures applications are built, deployed, and maintained with strong defenses against cyberattacks.
In the wider domain of cyber security, application security plays a vital role in preventing breaches that could expose sensitive information or disrupt business operations. Without proper security measures, applications become easy targets for attackers.
The Biggest Threats to Application Security
To build a strong defense, you first need to understand what you’re up against. Here are some of the most common threats to application security:
-
SQL Injection (SQLi): Attackers insert malicious SQL queries into application inputs to access or modify databases.
-
Cross-Site Scripting (XSS): Hackers inject harmful scripts into web applications to steal data or manipulate user sessions.
-
Malware Attacks: malicious software infects applications, causing data breaches, unauthorized access, or even system failures.
-
Denial-of-Service (DoS) attacks: hackers flood applications with excessive traffic, rendering them unusable.
-
Zero-Day Vulnerabilities: Security flaws unknown to developers are exploited before patches are released.
-
Weak authentication: Poorly managed authentication methods allow unauthorized users to access sensitive data.
-
Security Misconfigurations: Improperly configured security settings leave applications open to attack.
Secure Coding Practices: The First Line of Defense
One of the best ways to protect applications is to integrate security into the development process. Secure coding practices help minimize vulnerabilities, making applications more resilient against attacks. Here’s how developers can write secure code:
-
Validate User Input: Prevent SQL injection and XSS by filtering and validating all user inputs.
-
Implement Strong Authentication: Use multi-factor authentication (MFA) and enforce secure password policies.
-
Use parameterized queries: Protect against code injection attacks by avoiding dynamic SQL queries.
-
Encrypt sensitive data: Protect stored and transmitted data using strong encryption algorithms.
-
Keep software updated: Regularly update and patch applications to fix vulnerabilities.
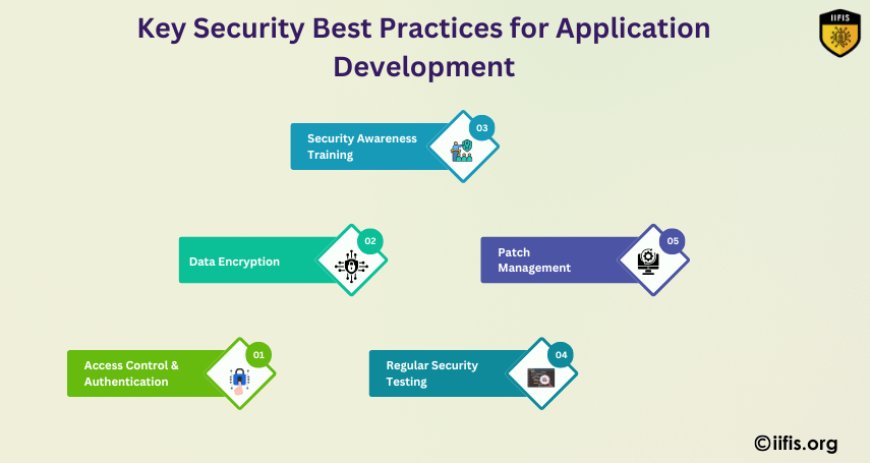
Key Security Best Practices for Application Development
To protect applications from cyber threats, developers and organizations must adopt strong security measures throughout the development lifecycle. Here are some key best practices:
-
Secure Coding Standards: Follow industry best practices to write code that minimizes vulnerabilities.
-
Regular Security Testing: Conduct penetration testing and vulnerability scans to identify weaknesses before attackers do.
-
Access Control & Authentication: Implement multi-factor authentication (MFA) and role-based access controls to restrict unauthorized access.
-
Data encryption: Encrypt sensitive data both in transit and at rest to prevent unauthorized access.
-
Patch Management: Regularly update applications and apply security patches to fix known vulnerabilities.
-
Security Awareness Training: educate developers and employees on secure coding, threat detection, and safe data handling.
The Role of Web Application Firewalls (WAF)
A Web Application Firewall (WAF) is a crucial security layer that monitors and filters HTTP traffic between applications and users. WAFs help protect applications from:
-
SQL Injection Attacks: Attackers manipulate a website’s database by injecting malicious SQL code, potentially gaining unauthorized access to sensitive information.
-
Cross-Site Scripting (XSS): Hackers insert malicious scripts into web pages that execute in a user’s browser, stealing data or compromising accounts.
-
Distributed Denial-of-Service (DDoS) Attacks: Attackers flood an application with excessive traffic, causing slowdowns or complete outages.
By analyzing traffic patterns and blocking malicious requests, WAFs provide an additional shield against cyber threats, ensuring applications remain secure and accessible.
Multi-Factor Authentication (MFA): Strengthening User Access
Authentication is one of the most critical aspects of application security in cyber security. Weak passwords and stolen credentials are among the leading causes of data breaches. Multi-factor authentication (MFA) adds an extra layer of security by requiring multiple forms of verification:
-
Something You Know: Passwords, PINs
-
Something You Have: Security tokens, mobile authentication apps
-
Something You Are: Fingerprint, facial recognition
By implementing MFA, businesses can significantly reduce unauthorized access and protect sensitive user data.
The Importance of Regular Security Testing
Security is not a one-time task but a continuous commitment to vulnerability scanning. Regular security testing helps organizations identify vulnerabilities before attackers can exploit them. Common testing methods include:
-
Penetration Testing: Simulating real-world cyberattacks to uncover weaknesses.
-
Static Application Security Testing (SAST): reviewing source code to find security flaws.
-
Dynamic Application Security Testing (DAST): Analyzing applications in runtime for vulnerabilities.
-
Vulnerability scanning: detecting known security risks in applications and systems.
Best Practices to Strengthen Application Security
To build a strong security posture, organizations should adopt these best practices:
-
Keep Software and Systems Updated: Regular patches and updates reduce vulnerabilities.
-
Use strong encryption: protect data at rest and in transit to prevent breaches.
-
Limit Access to Sensitive Information: Apply the principle of least privilege (PoLP) to restrict unnecessary access.
-
Train employees on security awareness: Educate developers and staff about cyber threats and security best practices.
-
Monitor applications for anomalies: Use advanced security monitoring tools to detect suspicious activities.
Cyber threats are constantly changing, making it essential to focus on application security. Recognizing potential risks and applying strong protective measures such as secure coding, WAFs, MFA, and routine testing helps organizations keep their applications safe from attacks. Understanding the key threats and implementing strong security measures such as secure coding, WAFs, MFA, and regular testing can help organizations safeguard their applications against attacks.
























