Why Penetration Testing is Critical for Modern Security
Penetration testing is essential for finding security weaknesses, preventing cyberattacks, and improving overall protection in the current technological environment.
Penetration testing is a proactive cybersecurity practice where ethical hackers—like myself—attempt to breach an organization’s system, network, or application to uncover vulnerabilities before malicious attackers can exploit them. Unlike unauthorized hackers, penetration testers are authorized by the organization to simulate real-world cyberattacks. Over the years, I’ve found that penetration testing isn't just about exploiting weaknesses—it's about understanding how attackers think and testing security from multiple angles.
As a Certified Penetration Tester (CPT), I am part of a team that identifies weaknesses in systems, provides solutions, and ensures that those weaknesses are properly addressed. This role is critical in today’s increasingly complex threat landscape, where cyberattacks are becoming more sophisticated and frequent.
Why Penetration Testing is Essential in Cybersecurity
-
The Growing Cybersecurity Threat Landscape:
-
Cyberattacks have evolved, with new threats like ransomware, phishing, and zero-day vulnerabilities constantly emerging. Every system connected to the internet, whether it's an enterprise network or a personal device, is a potential target.
-
Penetration testing helps organizations stay one step ahead of attackers by finding and addressing vulnerabilities before they can be exploited.
-
The Business Need for Penetration Testing:
-
In my experience, many organizations understand the need for strong cybersecurity policies but may not realize the vulnerabilities within their systems. Penetration testing highlights those weak spots, ensuring that sensitive data is protected from malicious actors.
-
Moreover, penetration testing helps companies evaluate their incident response capabilities—how quickly they can detect, respond, and recover from a cyberattack.
-
Penetration Testing and Compliance Requirements:
-
Many industries require regular penetration testing as part of their compliance frameworks. For example, standards like PCI DSS (Payment Card Industry Data Security Standard) or GDPR (General Data Protection Regulation) mandate regular security assessments to protect consumer data.
-
Penetration testers, like those certified by IIFIS, help organizations meet these regulatory requirements and ensure they are doing everything possible to safeguard sensitive information.
The Penetration Testing Process
Penetration testing is a structured, multi-phase process. Here’s a breakdown of the steps I typically follow:
-
Reconnaissance and Information Gathering: The first phase is about learning everything you can about the target system. Tools like Nmap, Shodan, and Google Dorking help gather information on the network, open ports, and services running on the target. The more information we can gather here, the better our chances of identifying vulnerabilities.
-
Scanning and Identifying Vulnerabilities: Using automated tools such as Nessus and OpenVAS, I scan the target system for known vulnerabilities. This helps me quickly identify common weaknesses like outdated software, misconfigured firewalls, or unpatched systems.
-
Exploitation and Post-Exploitation: Once a vulnerability is found, the next step is to exploit it, simulating what an attacker would do. Using frameworks like Metasploit, I attempt to gain access to the system. After exploiting a vulnerability, I check for ways to escalate privileges and maintain access.
-
Reporting and Remediation: The final step involves creating a report with detailed findings and recommendations for remediation. This is where I communicate what vulnerabilities were exploited, how far I was able to get into the system, and what steps the organization should take to fix the issues.
Tools I Use in Penetration Testing
Over the years, I've worked with a variety of tools to help with penetration testing. Some of my favorites include:
-
Kali Linux: The ultimate toolkit for penetration testers, Kali Linux comes with everything from vulnerability scanners to network analyzers.
-
Metasploit: This framework is used for creating and executing exploits against a remote target system. It’s a go-to tool for exploitation.
-
Nmap: For network discovery and vulnerability scanning, Nmap helps map out the attack surface.
-
Burp Suite: The best tool for web application testing, especially for identifying vulnerabilities like SQL injections and cross-site scripting (XSS).
-
Wireshark: A network protocol analyzer that helps capture and analyze network traffic in real-time, crucial for detecting hidden malicious activity.
Real-World Applications of Penetration Testing in Cybersecurity
Penetration testing is used across various domains, each serving a different purpose in cybersecurity:
-
Web Application Penetration Testing: Web applications often contain critical vulnerabilities that can be exploited, such as XSS or SQL injection. Penetration testing helps ensure that web apps are secure and that data is protected.
-
Network Security Testing: Testing corporate networks for vulnerabilities, from firewalls to VPN configurations, helps prevent unauthorized access.
-
Social Engineering and Phishing Simulations: Testing an organization’s resistance to phishing and social engineering attacks is critical. I’ve often tested employees by simulating real-world phishing campaigns.
-
Red Team Exercises: These involve simulating full-scale attacks on an organization, combining both digital and physical penetration testing to test overall security and incident response capabilities.
Challenges and Learning in Penetration Testing
-
Overcoming Complex Systems and Networks:
-
Some networks are well-fortified with advanced security systems, which can be challenging to bypass. In these cases, persistence, creativity, and a deep knowledge of attack techniques are crucial.
-
Staying Ahead of Cybersecurity Threats:
-
Cybersecurity is a fast-moving field. New vulnerabilities and attack vectors are discovered daily, so it’s essential to stay current with the latest tools, tactics, and trends.
-
Ethical and Legal Considerations:
-
Penetration testing is a privileged role that comes with great responsibility. As a certified tester, I always ensure that my actions are ethical, within the scope of the engagement, and in compliance with the law.
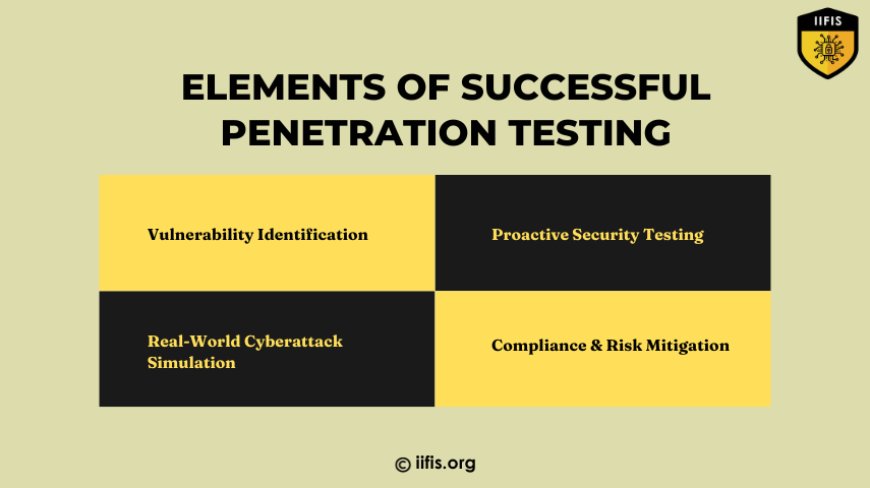
Elements of Successful Penetration Testing
Becoming a Certified Penetration Tester: A Personal Journey
Earning my Certified Penetration Tester (CPT) certification through IIFIS was a pivotal moment in my career. Here’s why:
-
Why I Chose the IIFIS Certification: IIFIS offers one of the most respected certifications in the cybersecurity community. Their curriculum is thorough, covering everything from basic exploitation techniques to advanced attack strategies, ensuring a well-rounded skill set.
-
Practical Experience: Hands-on experience was key to my preparation. I practiced on platforms like Hack The Box and TryHackMe to sharpen my skills and simulate real-world penetration tests.
-
Key Resources for Learning: Online training, CTF challenges, and cybersecurity forums helped me prepare for the certification exam and stay up-to-date with new techniques.
Penetration Testing as a Vital Part of Cybersecurity
Penetration testing is not just about testing security—it’s about staying ahead of hackers and ensuring that an organization’s systems are as secure as possible. Through my work, I’ve seen firsthand how penetration testing identifies critical weaknesses, prevents breaches, and enhances overall cybersecurity strategies.
Penetration testing will only become more important as cyber threats evolve. For those interested in pursuing this career, I encourage you to get certified, gain hands-on experience, and never stop learning. Penetration testing is a rewarding and impactful way to contribute to the fight against
























