Overview of General Information Security Principles
Explore fundamental principles of information security. Understand key concepts to safeguard data and systems effectively.
It is important to understand and put broad information security principles into practice to protect sensitive data from loss or improper use in modern technology. Providing a strong framework for protecting important information assets, these principles are the foundation of successful information security procedures. The first stage is a thorough risk assessment, which enables businesses to find weaknesses in their systems and processes that hackers might use against them. Organizations can proactively reduce these dangers and improve their general level of safety by being aware of them.
Security and access control are critical for data security. While encoding shields data from unwanted reading, access control maintains that only authorized people can access it. Regular updates fix problems, and staff members receive training to identify dangers. In minimizing damage from security incidents, an incident response plan protects company continuity. Following these guidelines improves defenses against cyberattacks and protects data.
Explanation of the complexities involved in ensuring information security
-
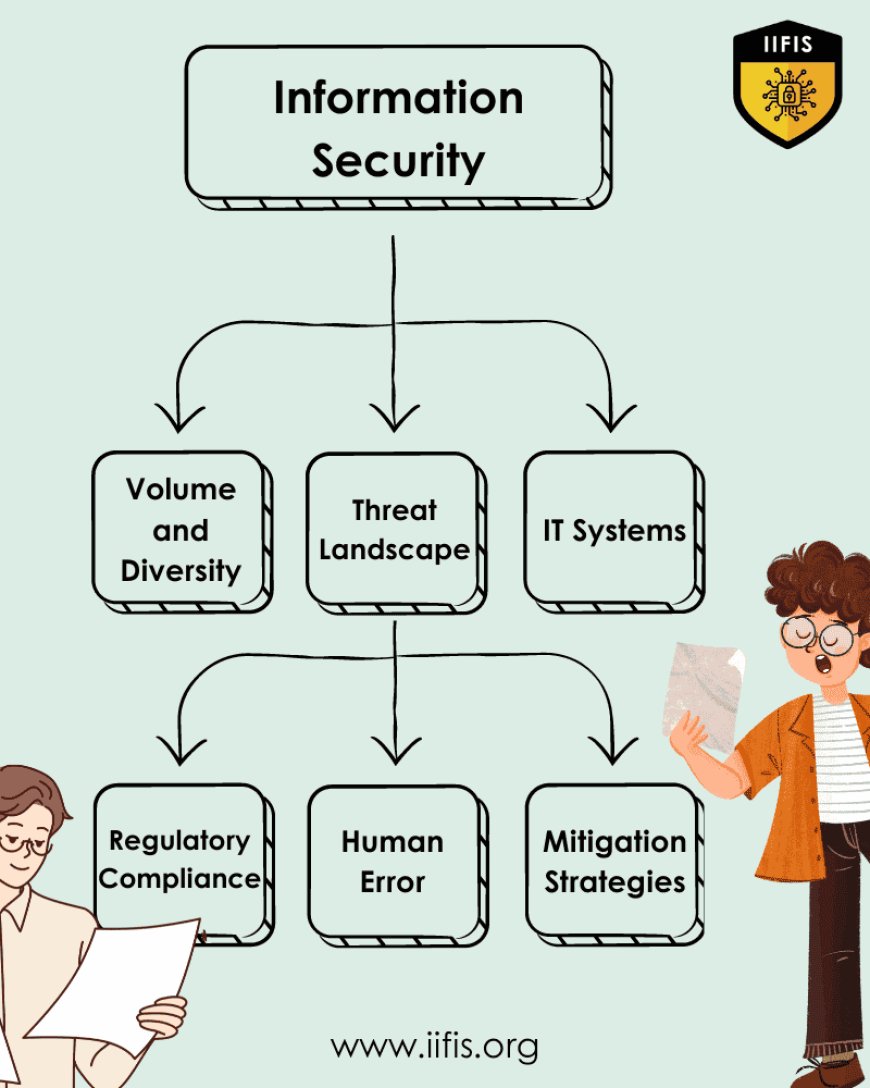
Volume and Diversity of Data: Organizations in the modern digital era deal with an unexpected volume of data from several sources. It is hard to stay on top of everything due to the large amount and diversity of data, which includes financial records and client information. To successfully manage and safeguard sensitive data, strong systems and procedures are needed to maintain its security.
-
Ever-evolving Threat Landscape: The dangers facing cybersecurity are always changing. Hackers are always coming up with new and advanced ways of taking advantage of the holes in networks and systems. To keep current with these dangers, organizations need to be alert and flexible. These threats may vary from viruses and phishing attempts to software and zero-day security holes. If it's not done, data and systems may be open to exploitation.
-
Interconnected IT Systems: IT systems are frequently integrated into intricate networks in the connected world of today. Information security is challenged by this connection, even though it has many positive effects on teamwork and interaction. A breach that develops in one part of the network may propagate to other parts, causing severe damage. For this reason, to safeguard their entire network architecture, businesses need to put up strong security measures.
-
Regulatory Compliance: A key element of information security is respect for industry standards and regulatory obligations. A few examples of industry-specific rules that control data handling and protection are the GDPR in Europe and HIPAA in the healthcare industry. It can be difficult and time-consuming for businesses to understand various regulatory frameworks, so they must keep educated and make sure they conform to all applicable compliance standards.
-
Human Error: The biggest obstacle to information security is human error, even with the strongest technology safeguards. Workers may inadvertently damage security by giving private information, clicking on phishing sites, or becoming a target of social engineering scams. Human error can be reduced by teaching staff members security best practices and promoting an environment of awareness and responsibility.
-
Mitigation Strategies: Organizations must employ multiple mitigation techniques to deal with these challenges. Investing in strong security technology, patching and updating systems regularly, holding staff awareness and training sessions, and keeping up with regulatory obligations are all examples of this. Organizations can effectively mitigate risks and protect their important data assets by adopting a proactive and complete approach to information security management.
What are the fundamental principles of information security?
-
Confidentiality:
This principle maintains that sensitive information is only able to be used by authorized people or systems. It involves maintaining confidential information and avoiding unapproved propagation to third parties. By limiting access to authorized users only, policies like access control and security support the maintenance of confidentiality.
-
Integrity:
Integrity provides that during its lifecycle, data is reliable, accurate, and complete. It refers to protecting data from unwanted additions, subtractions, or changes. By identifying and stopping illegal changes, methods like digital signatures, checksums, and data validation support the protection of data quality.
-
Availability:
Availability provides that services and data are available to authorized users at all times. It involves preventing interruptions or outages that can affect the accessibility of vital data or systems. Even in the face of unexpected events or attacks, continuous availability can be maintained with the use of strategies like redundancy, backups, and disaster recovery plans.
-
Authentication:
When a user or system wants to access resources or data, verification confirms their identity. Before giving users access to private data or systems, it verifies that they are who they say they are. Passwords, biometrics, and multi-factor authentication are examples of methods of identification that demand users to submit several kinds of verification.
-
Authorization:
What a user can do after having been verified is determined by their authorization. It involves providing or removing access rights under established roles and permissions. Organizations may ensure that users have access to only the resources and information required for their roles and responsibilities by applying authorization constraints.
-
Non-repudiation:
People are unable to contest the legality of their deeds or transactions if there is non-repudiation. It offers proof that a specific deed took place and that the person in charge of it cannot afterward deny it. By offering a trustworthy record of acts completed, strategies like audit trails and digital signatures aid in building a foundation of non-repudiation.
Types of Information Security
Network Security:
-
The main aim of network security is to protect the transmission of information and communication methods in computer networks. It includes steps to stop illegal access, data interception, and manipulation, such as the use of firewalls, intrusion detection systems, and virtual private networks (VPNs).
Endpoint Security:
-
Maintaining individual devices, such as PCs, laptops, tablets, and smartphones, is the focus of security for endpoints. Stop malware infections, data theft, and unwanted access to devices, it involves setting up device encoding, implementing security policies, and installing antivirus software.
Data Security:
-
Protecting the accessibility, privacy, and quality of data is the main goal of data security. This covers security against unwanted access, loss, or corruption of data, such as encryption, access controls, and data backup programs.
Application Security:
-
The main goals of the security of applications are to protect software programs and stop flaws that might be used by hackers. Find and fix possible security holes in programs, this involves employing techniques like code reviews, security testing, and secure coding practices.
Cloud Security:
-
The protection of information and programs stored in cloud environments is the focus of cloud security. To protect the integrity and confidentiality of data stored in the cloud, it comprises safeguards including data encryption, identity and access management (IAM), and frequent security audits.
Information security is fundamental for protecting digital systems and sensitive data. Safety protocols are based on fundamental concepts like availability, integrity, and secrecy. Mitigation techniques like frequent updates and staff training are crucial despite complexity like varied data volumes and dynamic threats. Different security types provide specific protection, such as network, endpoint, and cloud security. In modern technology, maintaining information security through thorough procedures and education is important for reducing risks and upholding confidence.
























