Basics of Securing Information Systems
Learn essential strategies for securing your information systems. Discover simple and effective practices to protect your data from cyber threats and ensure robust security.

Protecting information systems is more important than ever. With cyber threats becoming more common, it's crucial to have professionals who can keep data and systems safe. If you're aiming for a career in this field, it's important to understand the basics of information security. Earning certifications in cybersecurity, information security, or network security can give you a strong start. Whether you want to become a certified penetration tester, cybersecurity associate, or certified cybersecurity manager, having this foundational knowledge is key. Certifications like Application Security Certification will help you gain the skills needed to protect sensitive information and secure digital environments effectively.
The Growing Need for Securing Information Systems
Securing information systems has become crucial. Technology is expanding rapidly, and with it comes the risk of cyber threats. As businesses and people connect more online, the need to protect data and networks grows. This increased need is driving a significant rise in job opportunities for cybersecurity professionals.
If you’re interested in a cybersecurity career, now is a great time to get started. Whether you're seeking an entry-level cybersecurity job or aiming for a more advanced role, the demand for experts in securing information systems is high. Companies are actively looking for skilled individuals who can prevent breaches, manage risks, and ensure data safety.
This growing need emphasizes the importance of securing information systems and creates many opportunities for those looking to build a career in cybersecurity.
The Challenges in Securing Information Systems
Securing information systems is crucial but comes with many challenges. Organizations face obstacles such as rapidly changing cyber threats, outdated security practices, and the difficulty of protecting information across various networks. Keeping employees updated with the latest training and raising awareness adds to the complexity. Additionally, finding a balance between strong security measures and maintaining operational efficiency can create conflicts, especially when security measures affect productivity. As cyberattacks become more advanced, keeping security systems strong and adaptable remains a major challenge for businesses aiming to protect sensitive data.
Key Challenges:
- Rapidly changing cyber threats
- Outdated security practices
- Protecting information across various networks
- Ongoing employee training needs
- Balancing security with productivity
What Are the Fundamental Steps to Secure Information Systems?
1. Set Up a Security Policy
Create a clear security policy that defines roles, responsibilities, and procedures for handling security issues. This should be guided by relevant security certifications.
2. Perform a Risk Assessment
Identify potential vulnerabilities and threats to prioritize security measures. Use insights from certifications in Network Security and Application Security to guide this process.
3. Apply Access Controls
Make sure that only authorized users can access sensitive information by setting appropriate permissions. Consider certifications like Cybersecurity Associate or Certified Cyber Security Manager to enhance your control measures.
4. Keep Systems Updated
Regularly update software and systems to fix known security issues. For advanced vulnerability management, consider certifications like Certified Penetration Tester.
5. Train Your Team
Educate employees on how to recognize threats and follow best security practices. Use knowledge from security certifications to help reduce human error.
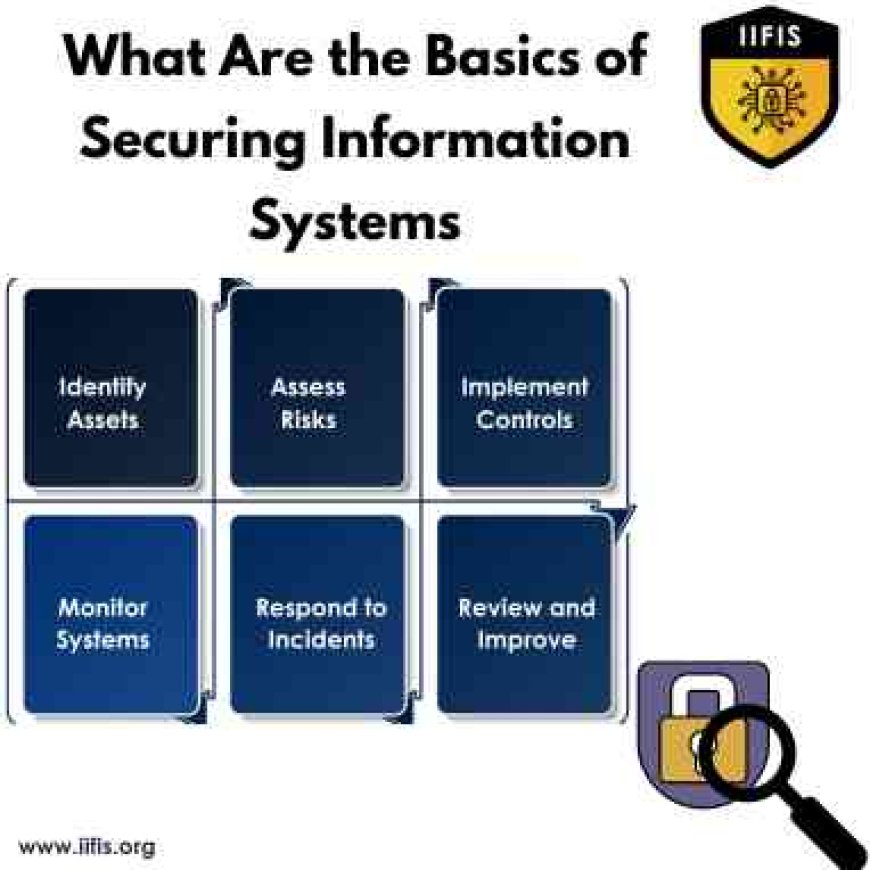
The Basics of Securing Information Systems
Securing information systems is crucial today, where cyber threats are increasingly common and complex. To protect data and maintain system integrity, it's essential to understand and apply basic security principles. Here’s a simple guide to help you get started with securing information systems.
1. Know the Core Concepts
Before getting into specific security measures, it's important to understand the basic concepts of information security. These include:
- Confidentiality: Ensures sensitive information is only accessible to those who are authorized.
- Integrity: Ensures that information remains accurate and has not been tampered with.
- Availability: Ensures that systems are accessible to authorized users when needed.
2. Implement Strong Authentication and Access Controls
A key part of securing information systems is setting up strong authentication and access controls:
- Use Strong Passwords: Require complex passwords that mix letters, numbers, and symbols. Change passwords regularly.
- Multi-Factor Authentication (MFA): Add extra security by requiring additional verification, like SMS codes or fingerprint scans.
- Role-Based Access Control (RBAC): Grant access based on job roles to make sure people only access what they need.
3. Secure Your Network Infrastructure
Your network is the foundation of your information systems, so it's vital to protect it:
- Firewalls: Use firewalls to control network traffic based on security rules.
- Intrusion Detection Systems (IDS): Implement IDS to detect and respond to security breaches and unusual activities.
- Regular Updates and Patching: Keep your network devices and software updated with the latest security patches to protect against vulnerabilities.
4. Guard Against Malware and Other Threats
Malware and other malicious threats can damage information systems, so take these steps to defend against them:
- Antivirus and Anti-Malware Software: Install and regularly update software to detect and remove threats.
- Regular Scans: Perform routine scans to find and fix security issues.
- Safe Browsing Practices: Teach users to recognize phishing attempts and avoid suspicious links and attachments.
5. Secure Application Development
Applications can be targets for cyber attacks, so it's important to secure them from development through deployment:
- Application Security Testing: Test applications thoroughly for vulnerabilities and fix any weaknesses.
- Secure Coding Practices: Follow secure coding guidelines to reduce vulnerabilities, such as validating input and handling errors properly.
- Regular Updates: Keep applications updated with security patches to fix any newly discovered issues.
6. Build a Strong Security Foundation with Certifications
Certifications can help build a strong security foundation and provide valuable knowledge:
- Cybersecurity Certifications: Get certifications in cybersecurity to understand risk management and incident response.
- Information Security Certifications: Pursue certifications that focus on information security best practices.
- Network Security Certifications: Obtain certifications for securing network infrastructures.
- Application Security Certification: Get certified in securing applications and software development.
- Certified Penetration Tester: Become a certified penetration tester to learn how to find and fix security weaknesses.
- Cybersecurity Associate: Achieve associate-level certifications to show foundational knowledge in cybersecurity.
- Certified Cybersecurity Manager: Obtain management-focused certifications to demonstrate skills in overseeing and implementing security measures.
7. Educate and Train Your Team
Human error can lead to security breaches, so regular education and training are crucial:
- Regular Training: Provide training on security best practices, threat awareness, and how to handle incidents.
- Simulated Attacks: Conduct simulated attacks to prepare staff for real-world security challenges.
- Security Awareness Campaigns: Run campaigns to keep security top of mind for employees and reinforce best practices.
Organizations can create a strong defense against cyber threats and protect their valuable assets. For more resources on securing information systems, visit the IIfis site for detailed guides, certifications, and tools to enhance your security efforts.
























