Key Differences between Information Security and Cybersecurity
Discover the key differences between information security and cybersecurity. Learn how these two crucial fields protect your data and systems, their unique focuses, and how they work together to ensure comprehensive security.
Understanding the details between information security and cybersecurity is essential for protecting your data and systems. While both fields aim to safeguard valuable assets, they focus on different aspects of security. Information security encompasses a broad range of practices designed to protect the confidentiality, integrity, and availability of information, regardless of its format. Cybersecurity, on the other hand, specifically addresses threats and defenses related to the digital domain, such as hacking, malware, and online attacks. This blog will explore the key differences between information security and cybersecurity, helping you understand their unique roles and how they complement each other in securing your digital and physical assets.
What is Information Security?
Information security is a field dedicated to protecting data from unauthorized access, disclosure, modification, or destruction. It encompasses the policies, procedures, and technologies used to safeguard information systems and ensure the confidentiality, integrity, and availability of data. This field is crucial for organizations and individuals to maintain privacy, security, and operational efficiency in an increasingly digital world.
Key Objectives of Information Security
-
Confidentiality
-
Definition: Ensuring that information is accessible only to those authorized to view it.
-
Importance: Protects sensitive data from unauthorized access and violations.
-
Examples: Using encryption to protect data in transit and at rest, and implementing strong access controls.
-
Integrity
-
Definition: Ensuring that information remains accurate and unchanged by unauthorized parties.
-
Importance: Maintains the trustworthiness of data and prevents tampering.
-
Examples: Implementing checksums and hashing algorithms to detect data changes and using version control systems.
-
Availability
-
Definition: Ensuring that information and resources are accessible to authorized users when needed.
-
Importance: Prevents disruptions to business operations and ensures continuity.
-
Examples: Utilizing backup systems, redundancy, and disaster recovery plans.
What is Cybersecurity?
Definition and Scope of Cybersecurity
Cybersecurity is the practice of protecting computer systems, networks, and digital assets from cyber threats and attacks. It involves implementing measures to defend against unauthorized access, data breaches, and various forms of cyberattacks that can compromise the integrity, confidentiality, and availability of information. The scope of cybersecurity extends to protecting sensitive data, ensuring the secure operation of IT infrastructure, and reducing risks associated with digital activities.
Focus on Protecting Digital Assets from Cyber Threats and Attacks
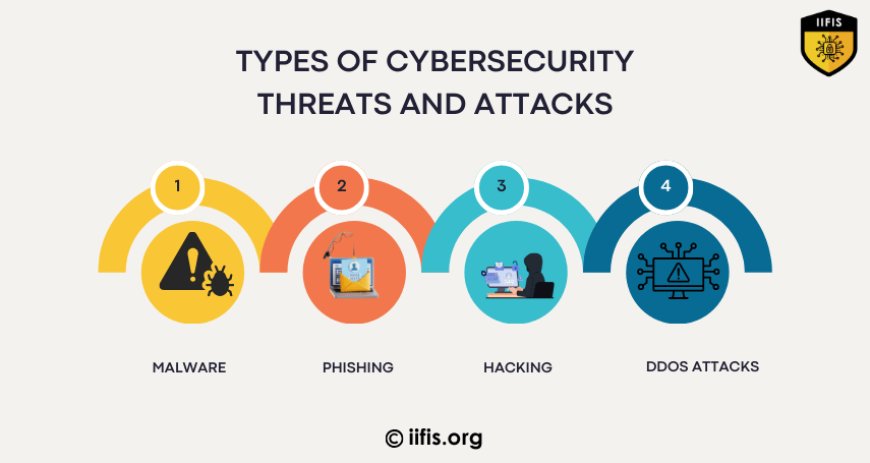
Cybersecurity focuses on defending digital assets from a range of cyber threats, including
-
Malware: Malicious software designed to damage or disrupt systems (e.g., viruses, worms, ransomware).
-
Phishing: Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity.
-
Hacking: Unauthorized access to systems or data by exploiting vulnerabilities.
-
DDoS Attacks: Distributed Denial of Service attacks aimed at overwhelming systems or networks to disrupt services.
-
Insider Threats: Risks posed by individuals within an organization who misuse their access to harm the system.
Key Differences Between Information Security and Cybersecurity
1. Scope
-
Broad Protection: Includes the protection of all forms of information, whether physical, digital or in transit. It includes safeguarding both digital and non-digital assets such as paper documents, physical storage devices, and other forms of data.
-
Includes: Physical security measures (e.g., locked doors, security guards) and administrative controls (e.g., policies, procedures).
-
Cybersecurity:
-
Specific Focus: Concentrates specifically on protecting digital assets and systems from cyber threats. It deals with safeguarding information in electronic form, particularly in networks and internet-connected environments.
-
Includes: Digital measures such as network security, data encryption, and technical defenses.
2. Approach
-
Information Security:
-
Holistic Approach: Incorporates a comprehensive strategy that includes physical, administrative, and technical controls. It aims to ensure the overall security of information across various formats and systems.
-
Controls Include: Security policies, employee training, physical security measures, and risk management practices.
-
Cybersecurity:
-
Technical Defenses: Focuses primarily on technical defenses to protect against cyber threats. This approach involves implementing and managing technologies designed to detect, prevent, and respond to cyberattacks.
-
Controls Include: Firewalls, intrusion detection systems (IDS), anti-malware software, and network security solutions.
3. Threats Addressed
-
Information Security:
-
Risks Related to Data Handling and Storage: Addresses a wide range of threats including unauthorized access, data breaches, and physical theft of information. It also covers risks associated with how data is handled, stored, and managed.
-
Examples: Protecting physical documents from unauthorized access and securing data storage devices.
-
Cybersecurity:
-
Online and Network-Based Attacks: Focuses on threats specifically related to online and network environments. This includes protecting systems from cyberattacks such as malware infections, phishing, and denial-of-service attacks.
-
Examples: Defending against ransomware attacks and securing network traffic from interception.
4. Network Security
-
Network Security Integration: Includes network security as part of its broader strategy. It involves ensuring that networks are secure as part of overall information protection efforts.
-
Approach: May include network security measures but also integrates them with physical and administrative controls.
-
Cybersecurity:
-
Primary Focus: Network security is a core component of cybersecurity. It involves protecting the integrity, confidentiality, and availability of network resources from various cyber threats.
-
Measures Include: Firewalls, intrusion prevention systems (IPS), network segmentation, and secure access controls.
In summary, while both information security and cybersecurity aim to protect valuable information, they differ in their scope, approach, and the specific threats they address. Information security offers a broader protective framework, while cybersecurity focuses on defending digital environments against cyber-specific threats.
How Information Security and Cybersecurity Complement Each Other
Integration for Comprehensive Protection
Combining information security and cybersecurity ensures a complete defense strategy that covers both physical and digital threats. This integrated approach provides thorough protection for data and systems.
Examples of Complementary Practices
-
Securing Physical Access to Servers
-
Information Security: Restrict access to server rooms.
-
Cybersecurity Benefit: Prevents unauthorized tampering with servers, improving digital security.
-
Implementing Data Encryption
-
Cybersecurity: Encrypt data in transit and at rest.
-
Information Security Benefit: Protects data even if physical security measures fail.
-
Conducting Security Awareness Training
-
Information Security: Train employees on data handling and security policies.
-
Cybersecurity Benefit: Reduces risks of phishing and other cyberattacks.
-
Regular Security Audits
-
Information Security: Assess physical and administrative controls.
-
Cybersecurity Benefit: Identifies vulnerabilities in digital systems.
-
Implementing Access Controls
-
Cybersecurity: Manage digital access to data.
-
Information Security Benefit: Ensures only authorized personnel can access sensitive information.
-
Disaster Recovery Planning
-
Information Security: Prepare for physical disasters.
-
Cybersecurity Benefit: Ensures data recovery from cyber incidents.
Integrating these practices ensures a robust and resilient security framework.
Practical Implications
Benefits for Businesses
-
Enhanced Security: Addresses both physical and digital threats for comprehensive protection.
-
Improved Risk Management: Mitigates various risks, ensuring robust security.
-
Compliance and Trust: Meets regulations and builds trust with stakeholders.
Tips for Implementation
-
Conduct Risk Assessments
-
Identify risks and develop a security strategy for both physical and digital assets.
-
Develop Integrated Policies
-
Create policies that cover physical security and cybersecurity.
-
Implement Access Controls
-
Manage access with key cards for physical areas and role-based controls for digital systems.
-
Invest in Training
-
Educate employees on both physical and digital security practices.
-
Review and Update Regularly
-
Perform regular audits and updates to keep security measures current.
-
Establish Disaster Recovery Plans
-
Develop plans for both physical and digital recovery to ensure business continuity.
Integrating these measures ensures a secure and resilient business environment.
Information security and cybersecurity each play a vital role in protecting data and systems. Information security covers all aspects of data protection, including physical and digital, while cybersecurity focuses specifically on digital threats with technical measures.
Understanding these differences is key to implementing a comprehensive security strategy. We encourage businesses to integrate both approaches to ensure complete protection of their assets. For advanced expertise, consider exploring training from the International Institute for Information Security (IIFIS), which offers valuable resources to enhance your security practices. Adopting a unified approach helps safeguard all aspects of your data and system security effectively.























