Explore Career Paths in Information Security Analyst
Discover diverse career paths in information security analysis, from entry-level roles to advanced positions. Learn about required skills, education, and job opportunities in this growing field.

Information security is an increasingly essential field as organizations face growing threats from cyberattacks and data breaches. The rapid advancement of technology and the addition of digital data have heightened the need for strong security measures to protect sensitive information. As a result, the field of information security is expanding, offering varied career opportunities for those interested in protecting digital assets.
Exploring various career paths within information security is essential for finding a role that matches your skills and interests. From cybersecurity analysts and penetration testers to security consultants and compliance officers, each position plays a crucial role in defending against cyber threats. Understanding these career options allows you to identify where your expertise can have the greatest impact and helps you tailor your career development to meet the growing demands of this dynamic industry.
Information security
Information security, also known as infosec, involves protecting digital and physical information from unauthorized access, use, disclosure, disruption, modification, or destruction. The goal is to ensure the confidentiality, integrity, and availability of data. Key aspects of information security include:
-
Confidentiality: Ensuring that information is accessible only to those authorized to view it. This involves measures like encryption and access controls.
-
Integrity: Maintaining the accuracy and completeness of information. This means preventing unauthorized modifications and ensuring data remains reliable.
-
Availability: Ensuring that information and resources are accessible to authorized users when needed. This involves implementing backup systems and redundancy.
Information security encompasses various practices, technologies, and policies designed to protect data from cyber threats, including hacking, malware, and insider threats. It is critical for protecting sensitive information in both organizational and personal contexts.
Definition and Role: An information security analyst is a professional responsible for protecting an organization's computer systems and networks from cyber threats. Their role involves analyzing and implementing security measures to safeguard sensitive information and ensure the overall security of IT infrastructure.
Key Responsibilities and Daily Tasks:
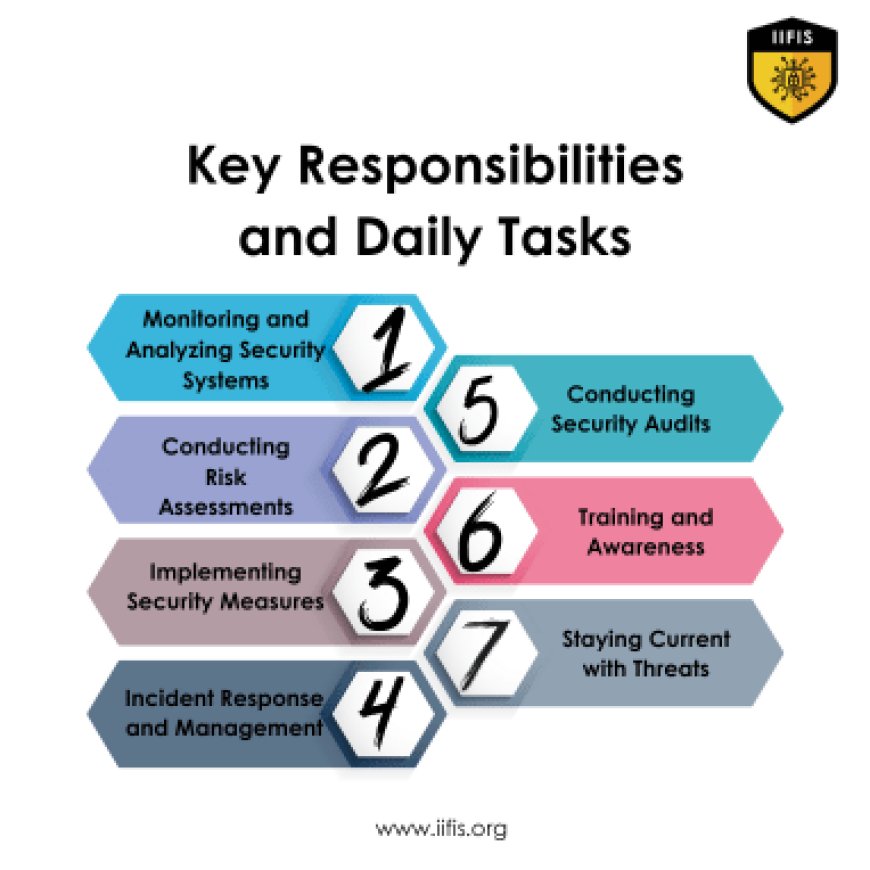
1. Monitoring and Analyzing Security Systems:
-
-
Continuously monitor security systems and network traffic for unusual activity or potential threats. Analyze security logs and alerts to identify and respond to incidents.
-
-
Conducting Risk Assessments:
-
Perform regular risk assessments to identify vulnerabilities and potential security risks. Evaluate the effectiveness of existing security measures and recommend improvements.
-
-
Implementing Security Measures:
-
Develop and implement security protocols, such as firewalls, intrusion detection systems, and encryption methods, to protect against cyber threats.
-
-
Incident Response and Management:
-
Respond to and manage security incidents, such as data breaches or malware infections. Investigate incidents, contain damage, and develop strategies to prevent future occurrences.
-
-
Conducting Security Audits:
-
Perform regular security audits to assess compliance with internal policies and external regulations. Document findings and recommend corrective actions.
-
-
Training and Awareness:
-
Educate employees about security best practices and emerging threats. Conduct training sessions to raise awareness and promote a culture of security within the organization.
-
-
Staying Current with Threats:
-
Keep up-to-date with the latest cybersecurity trends, threats, and technologies. Participate in professional development to stay informed about advancements in the field.
-
Common Career Paths in Information Security Analysis
-
Entry-Level Positions:
-
Roles: IT Support Specialist, Security Technician.
-
Focus: Gaining foundational experience in IT and security tasks.
-
Security Analyst:
-
Role: Monitors and analyzes security systems to detect and respond to threats.
-
Skills: Analytical abilities, security protocols knowledge, and familiarity with security tools.
-
IT Security Specialist:
-
Role: Implements and manages security measures to protect IT infrastructure.
-
Skills: Expertise in security technologies, risk management, and compliance.
These roles provide a range of opportunities to build and advance a career in information security.
Mid-Level Positions in Information Security Analysis
-
Security Engineer:
-
Role: Designs, implements, and maintains security systems and infrastructure to protect against cyber threats.
-
Skills: Expertise in network security, encryption technologies, and security architecture.
-
Incident Responder:
-
Role: Responds to and manages security incidents, investigates breaches, and develops strategies to prevent future incidents.
-
Skills: Strong problem-solving abilities, knowledge of forensic techniques, and experience with incident response protocols.
These mid-level roles focus on advanced security measures and incident management, offering opportunities for deeper specialization and leadership within information security.
Advanced Positions in Information Security Analysis
-
Security Architect:
-
Role: Designs and oversees the implementation of complex security frameworks and strategies to protect an organization’s IT infrastructure.
-
Skills: Deep understanding of security architecture, risk management, and advanced security technologies.
-
Chief Information Security Officer (CISO):
-
Role: Leads the organization’s information security strategy, manages the security team, and ensures overall security governance and compliance.
-
Skills: Leadership, strategic planning, comprehensive knowledge of security policies, and regulatory requirements.
These advanced positions involve strategic oversight and high-level decision-making, focusing on the overall security posture and long-term protection of the organization’s assets.
Specialized Roles in Information Security Analysis
-
Penetration Tester:
-
Role: Simulates cyberattacks to identify vulnerabilities and weaknesses in systems, networks, and applications.
-
Skills: Expertise in ethical hacking, vulnerability assessment, and penetration testing tools and techniques.
-
Forensic Analyst:
-
Role: Investigates cyber incidents and data breaches to gather and analyze evidence, supporting legal and regulatory actions.
-
Skills: Knowledge of forensic investigation methods, data recovery, and legal compliance.
These specialized roles focus on assessing security through simulated attacks and investigating cyber incidents, offering in-depth expertise in their respective areas.
Required Skills and Qualifications
-
Technical Skills:
-
Cybersecurity Tools: Familiarity with firewalls, IDS, and antivirus software.
-
Threat Analysis: Ability to identify and assess security threats.
-
Network Security: Knowledge of network protocols and protection measures.
-
Soft Skills:
-
Problem-Solving: Strong analytical abilities for resolving security issues.
-
Communication: Clear reporting and teamwork skills.
-
Critical Thinking: Analyzing complex situations and making decisions.
-
Certifications:
-
CISSP: Comprehensive security knowledge.
-
CEH: Skills in ethical hacking.
-
CompTIA Security+: Fundamental security concepts.
Education and Training Pathways
-
Recommended Degrees and Academic Programs:
-
Degrees: Pursue a bachelor’s or master’s degree in cybersecurity, information security, computer science, or a related field.
-
Professional Certifications and Training Courses:
-
Certifications: Obtain certifications such as CISSP, CEH, and CompTIA Security+ to validate your skills and knowledge.
-
Training Courses: Enroll in specialized courses offered by recognized institutions or online platforms to gain practical skills.
-
Continuous Learning and Staying Updated:
-
Industry Trends: Regularly review industry publications, attend webinars, and participate in professional groups to keep up with the latest developments and threats in information security.
These pathways will help you build a solid foundation and stay competitive in the evolving field of information security.
Job Market and Opportunities
-
Current Demand for Information Security Analysts:
-
High Demand: There is a strong and growing demand for information security analysts due to increasing cyber threats and data protection regulations.
-
Typical Employers and Industry Sectors:
-
Financial Sector: Banks and financial institutions require robust security to protect sensitive financial data.
-
Healthcare Sector: Hospitals and healthcare providers need to safeguard patient information and comply with regulations.
-
Government Sector: Government agencies focus on securing national data and critical infrastructure.
-
Technology Sector: Tech companies and startups need security professionals to protect their systems and innovations.
These sectors offer diverse opportunities for information security professionals, reflecting the critical importance of cybersecurity across various industries.
How to Advance Your Career
-
Networking and Professional Associations:
-
Join: Connect with industry professionals through organizations like (ISC)², ISACA, and local cybersecurity groups.
-
Attend: Participate in industry conferences, seminars, and webinars to build relationships and stay informed.
-
Gaining Practical Experience:
-
Internships: Seek internships or entry-level positions to gain hands-on experience and apply theoretical knowledge.
-
Projects: Work on personal or open-source security projects to demonstrate your skills and build a portfolio.
-
Pursuing Advanced Certifications and Higher Education:
-
Certifications: Obtain advanced certifications like CISM or CISSP for specialized expertise.
-
Education: Consider pursuing a master’s degree in cybersecurity or related fields to deepen your knowledge and open up advanced career opportunities.
These steps will help you build a strong professional network, gain valuable experience, and improve your qualifications for career advancement in information security.
Information security analysis provides a wide range of career paths, from entry-level roles such as IT Support Specialist to advanced positions like Security Architect and CISO. Each role is vital in defending against cyber threats and safeguarding valuable data. The field’s rapid expansion offers numerous opportunities for professional growth and specialization.
To excel in this exciting field, consider pursuing educational programs and certifications from IIFIS (International Institute for Information Security). IIFIS offers comprehensive training that can significantly boost your skills and career prospects. Now is an excellent time to explore these opportunities and embark on a rewarding career in information security.
























